How to 100% pass 70-417 exam? GreatExam provides the guaranteed 70-417 exam preparation material to boost up your confidence in 70-417 exam. Successful candidates have provided their reviews about our 70-417 dumps. Now GreatExam supplying the new version of 70-417 VCE and PDF dumps. We ensure our 70-417 exam questions are the most complete and authoritative compared with others’, which will ensure your 70-417 exam pass.
QUESTION 81
Hotspot Question
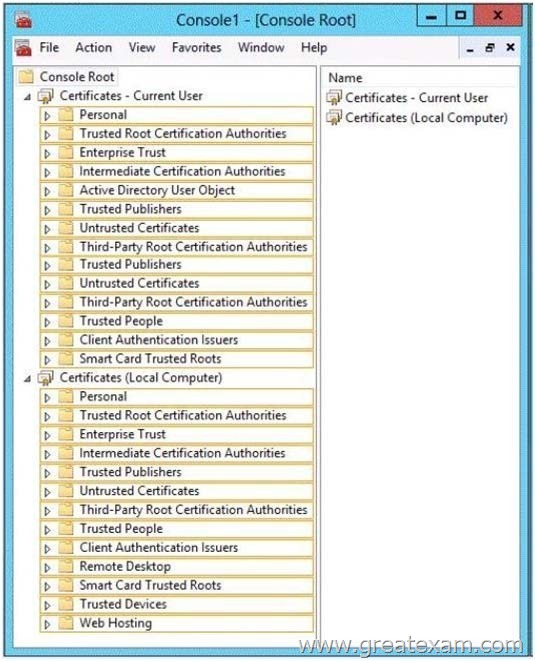
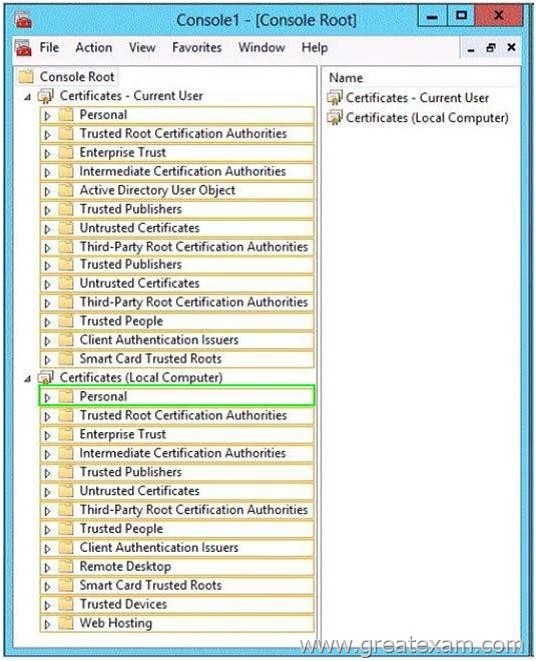
You have a server named Server1 that has the Web Server (IIS) server role installed.
You obtain a Web Server certificate.
You need to configure a website on Server1 to use Secure Sockets Layer (SSL).
To which store should you import the certificate? To answer, select the appropriate store in the answer area.
QUESTION 82
You have a server named Served that runs Windows Server 2012 R2. On Server1, you configure a custom Data Collector Set (DCS) named DCS1.
DCS1 is configured to store performance log data in C:\Logs.
You need to ensure that the contents of C:\Logs are deleted automatically when the folder reaches 100 MB in size.
What should you configure?
A. A File Server Resource Manager (FSRM) file screen on the C:\Logs folder
B. A schedule for DCS1
C. The Data Manager settings of DCS1
D. A File Server Resource Manager (FSRM) quota on the C:\Logs folder
Answer: C
Explanation:
To configure data management for a Data Collector Set
1. In Windows Performance Monitor, expand Data Collector Sets and click User Defined.
2. In the console pane, right-click the name of the Data Collector Set that you want to configure and click Data Manager.
3. On the Data Manager tab, you can accept the default values or make changes according to your data retention policy. See the table below for details on each option. When Minimum free disk or Maximum folders is selected, previous data will be deleted according to the Resource policy you choose (Delete largest or Delete oldest) when the limit is reached. When Apply policy before the data collector set starts is selected, previous data will be deleted according to your selections before the data collector set creates its next log file.
When Maximum root path size is selected, previous data will be deleted according to your selections when the root log folder size limit is reached.
4. Click the Actions tab. You can accept the default values or make changes. See the table below for details on each option.
5. When you have finished making your changes, click OK.
QUESTION 83
You have a server named Server1 that runs Windows Server 2012 R2.
You create a custom Data Collector Set (DCS) named DCS1.
You need to configure DCS1 to meet the following requirements:
– Automatically run a program when the amount of total free disk space on Server1 drops below 10 percent of capacity.
– Log the current values of several registry settings.
Which two should you configure in DCS1? (Each correct answer presents part of the solution. Choose two.)
A. System configuration information
B. A Performance Counter Alert
C. Event trace data
D. A performance counter
Answer: AB
QUESTION 84
You have a VHD that contains an image of Windows Server 2012 R2.
You plan to Apply updates to the image.
You need to ensure that only updates that can install without requiring a restart are installed.
Which DISM option should you use?
A. /Apply-Unattend
B. /Add-ProvisionedAppxPackage
C. /PreventPending
D. /Cleanup-Image
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/hh825265.aspx
QUESTION 85
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You have several Windows PowerShell scripts that execute when client computers start. When a client computer starts, you discover that it takes a long time before users are prompted to log on.
You need to reduce the amount of time it takes for the client computers to start. The solution must not prevent scripts from completing successfully.
Which setting should you configure? To answer, select the appropriate setting in the answer area.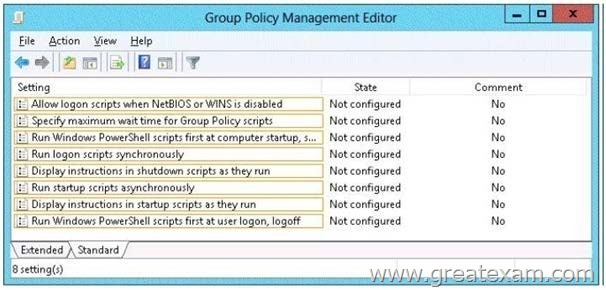
Answer: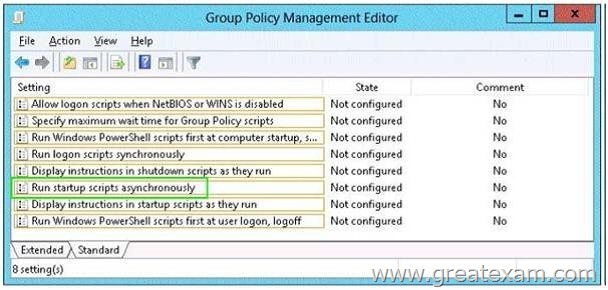
QUESTION 86
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the IP Address Management (IPAM) Server feature installed. Server2 has the DHCP Server server role installed. A user named User1 is a member of the IPAM Users group on Server1.
You need to ensure that User1 can use IPAM to modify the DHCP scopes on Server2.
The solution must minimize the number of permissions assigned to User1.
To which group should you add User1?
A. IPAM ASM Administrators on Server1
B. IPAMUG in Active Directory
C. DHCP Administrators on Server2
D. IPAM MSM Administrators on Server1
Answer: D
IPAM MSM administrators – Completely manages DHCP and DNS servers. IPAM MSM Administrators is a local security group on an IPAM server that is created when you
install the IPAM feature. Members of this group have all the privileges of the IPAM Users security group, and can perform server monitoring and management tasks
in addition to IPAM common management tasks.IPAM multi-server management (MSM) administrators can manage DNS and DHCP servers.
IPAM ASM Administrators on Server1 – Completely manages IP addresses.IPAM address space management (ASM) administrators can manage IP address blocks, ranges, and
addresses.
IPAM Users Group (IPAMUG) – To access configuration data and server event logs, the IPAM server must be a member of the domain IPAM Users Group (IPAMUG).
DHCP Administrators – Members of the DHCP Administrators group can view and modify any settings on the DHCP server. DHCP Administrators can create and delete
scopes, add reservations, change option values, create superscopes, or perform any other task required to administer the DHCP server, including export or
import of the DHCP server configuration and database.
IPAM Users group – IPAM Users is a local security group on an IPAM server that is created when you install the IPAM feature. Members of this group can view all
information in server inventory, IP address space, and the monitor and manage IPAM console nodes. IPAM Users can view IPAM and DHCP operational events under in
the Event Catalog node, but cannot view IP address tracking data.
More info : https://technet.microsoft.com/en-us/library/dn268500.aspx
https://technet.microsoft.com/en-us/library/jj878311.aspx
https://technet.microsoft.com/en-us/library/dd759157.aspx
https://technet.microsoft.com/en-us/library/jj878342.aspx
https://technet.microsoft.com/en-us/library/jj878348.aspx
QUESTION 87
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Print1. Your company implements DirectAccess. A user named User1 frequently works at a customer’s office. The customer’s office contains a print server named Print1. While working at the customer’s office, User1 attempts to connect to Print1. User1 connects to the Print1 server in contoso.com instead of the Print1 server at the customer’s office.
You need to provide User1 with the ability to connect to the Print1 server in the customer’s office. Which Group Policy option should you configure? To answer, select the appropriate option in the answer area.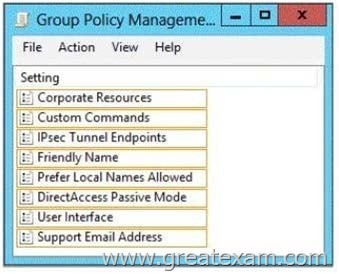
Answer: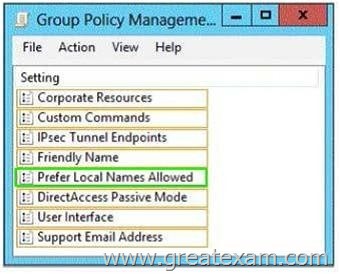
QUESTION 88
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Access server role installed.
You log on to Server1 by using a user account named User2. From the Remote Access Management Console, you run the Getting Started wizard and you receive a warning message as shown in the exhibit. (Click the Exhibit button.)
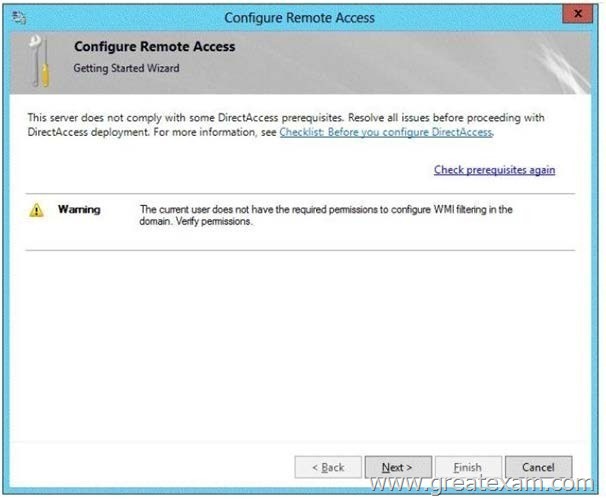
You need to ensure that you can configure DirectAccess successfully.
The solution must minimize the number of permissions assigned to User2.
To which group should you add User2?
A. Enterprise Admins
B. Server Operators
C. Domain Admins
D. Account Operators
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/hh918408.aspx#feedback
QUESTION 89
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has the Remote Access server role installed. DirectAccess is implemented on Server1 by using the default configuration.
You discover that DirectAccess clients do not use DirectAccess when accessing websites on the Internet.
You need to ensure that DirectAccess clients access all Internet websites by using their DirectAccess connection.
What should you do?
A. Configure DirectAccess to enable force tunneling.
B. Configure a DNS suffix search list on the DirectAccess clients.
C. Disable the DirectAccess Passive Mode policy setting in the DirectAccess Client Settings Group Policy object (GPO).
D. Enable the Route all traffic through the internal network policy setting in the DirectAccess Server Settings Group Policy object (GPO).
Answer: A
QUESTION 90
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. On all of the domain controllers, Windows is installed in
C:\Windows and the Active Directory database is located in D:\Windows\NTDS\.
All of the domain controllers have a third-party Application installed. The operating system fails to recognize that the Application is compatible with domain controller cloning.
You verify with the Application vendor that the Application supports domain controller cloning. You need to prepare a domain controller for cloning.
What should you do?
A. In C:\Windows\System32\Sysprep\Actionfiles\, add the Application information to an XML file named Respecialize.xml.
B. In D:\Windows\NTDS\, create an XML file named DCCloneConfig.xml and add the Application information to the file.
C. In D:\Windows\NTDS\, create an XML file named CustomDCCloneAllowList.xml and add the Application information to the file.
D. In C:\Windows\, create an XML file named DCCloneConfig.xml and add the Application information to the file.
Answer: C
Explanation:
http://blogs.dirteam.com/blogs/sanderberkouwer/archive/2012/09/10/new-features-inactive-directory-domainservices-in-windows-server-2012-part-13-domain-controllercloning.aspx
QUESTION 91
You have a server named Server1 that runs Windows Server 2012 R2.
You create a custom Data Collector Set (DCS) named DCS1.
You need to configure Server1 to start DCS1 automatically when the network usage exceeds 70 percent.
Which type of data collector should you create?
A. A configuration data collector
B. A performance counter data collector
C. An event trace data collector
D. A performance counter alert
Answer: D
QUESTION 92
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
You plan to install the Active Directory Federation Services server role on Server1 to allow for Workplace Join.
You run nslookupenterpriseregistration and you receive the following results: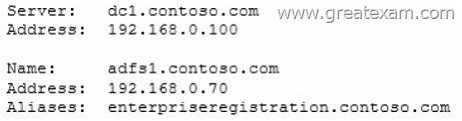
You need to create a certificate request for Server1 to support the Active Directory Federation Services (AD FS) installation.
How should you configure the certificate request? To answer, drag the appropriate names to the correct locations. Each name may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.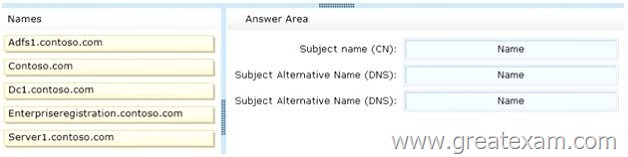
Answer: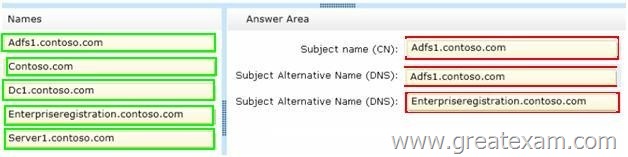
QUESTION 93
You have a server named Server1 that runs Windows Server 2012 R2.
You discover that the performance of Server1 is poor.
The results of a performance report generated on Server1 are shown in the following table.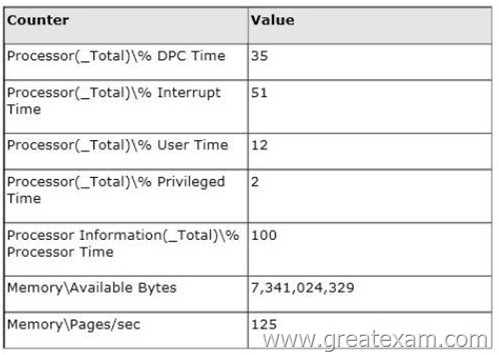
You need to identify the cause of the performance issue.
What should you identify?
A. Insufficient RAM
B. Driver malfunction
C. Excessive paging
D. Non-uniform memory access (NUMA)
Answer: B
Explanation:
http://greatit.wordpress.com/2009/08/17/high-interrupt-cpu-time-troubleshooting-with-xperf/
http://blogs.technet.com/b/askperf/archive/2008/01/25/an-overview-of-troubleshooting-memory-issues.aspx
QUESTION 94
Your network contains an Active Directory domain named adatum.com. The domain contains a member server named Server1 and 10 web servers. All of the web servers are in an organizational unit (OU) named WebServers_OU. All of the servers run Windows Server 2012 R2. On Server1, you need to collect the error events from all of the web servers. The solution must ensure that when new web servers are added to WebServers_OU, their error events are collected automatically on Server1.
What should you do?
A. On Server1, create a collector initiated subscription.
From a Group Policy object (GPO), configure the Configure forwarder resource usage setting.
B. On Server1, create a collector initiated subscription.
From a Group Policy object (GPO), configure the Configure target Subscription Manager setting.
C. On Server1, create a source computer initiated subscription.
From a Group Policy object (GPO), configure the Configure forwarder resource usage setting.
D. On Server1, create a source computer initiated subscription.
From a Group Policy object (GPO), configure the Configure target Subscription Manager setting.
Answer: D
QUESTION 95
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2. The domain contains an organizational unit (OU) named OU1. OU1 contains an OU named OU2. OU2 contains a user named User1.
User1 is the member of a group named Group1. Group1 is in the Users container.
You create five Group Policy objects (GPO).
The GPOs are configured as shown in the following table.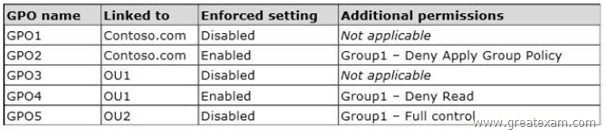
The Authenticated Users group is assigned the default permissions to all of the GPOs.
There are no site-level GPOs.
You need to identify which three GPOs will be Applied to User1 and in which order the GPOs will be Applied to User1.
Which three GPOs should you identify in sequence? To answer, move the appropriate three GPOs from the list of GPOs to the answer area and arrange them in the correct order.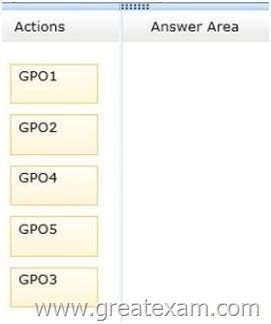
Answer:
QUESTION 96
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2. DirectAccess is deployed to the network. Remote users connect to the DirectAccess server by using a variety of network speeds.
The remote users report that sometimes their connection is very slow.
You need to minimize Group Policy processing across all wireless wide area network (WWAN) connections.
Which Group Policy setting should you configure?
A. Configure Group Policy slow link detection.
B. Configure wireless policy processing.
C. Change Group Policy processing to run asynchronously when a slow network connection is detected.
D. Configure Direct Access connections as a fast network connection.
Answer: A
QUESTION 97
Your network contains a single Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains 400 desktop computers that run Windows 8 and 10 desktop computers that run Windows XP Service Pack 3 (SP3). All new desktop computers that are added to the domain run Windows 8. All of the desktop computers are located in an organizational unit (OU) named OU1.
You create a Group Policy object (GPO) named GPO1. GPO1 contains startup script settings. You link GPO1 to OU1.
You need to ensure that GPO1 is Applied only to computers that run Windows XP SP3.
What should you do?
A. Modify the Security settings of OU1.
B. Run the Set-GPInheritancecmdlet and specify the -target parameter.
C. Create and link a WMI filter to GPO1.
D. Run the Set-GPLinkcmdlet and specify the -target parameter.
Answer: C
Explanation:
WMI Filtering is used to get information of the system and apply the GPO on it with the condition is met.Security filtering: apply a GPO to a specific group (members of the group)
QUESTION 98
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
All client computers run Windows 7. Group Policy objects (GPOs) are linked to the domain as shown in the exhibit. (Click the Exhibit button.)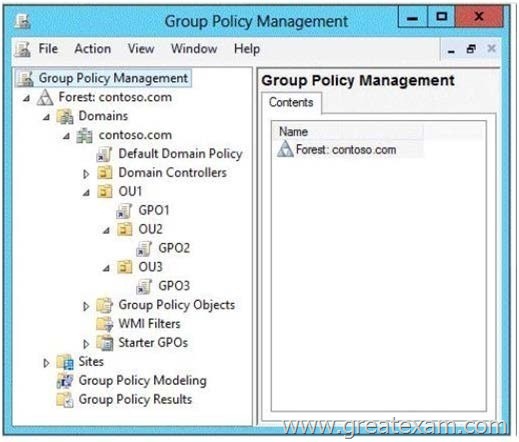
GPO2 contains user configurations only and GPO3 contains computer configurations only.
You need to configure the GPOs to meet the following requirements:
– Ensure that GPO2 only Applies to the user accounts in OU2 that are members of a global group named Group2.
– Ensure that GPO3 only Applies to the computer accounts in OU3 that have more than 100 GB of free disk space.
What should you do? To answer, drag the appropriate setting to the correct GPO. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.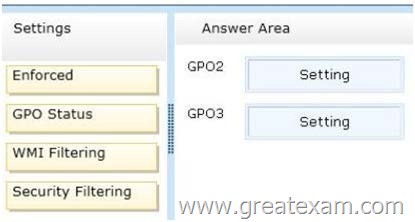
Answer: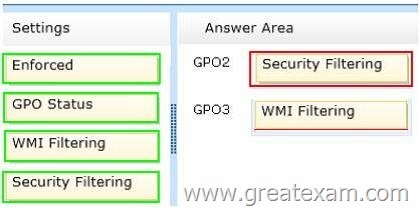
QUESTION 99
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains two organizational units (OUs) named OU1 and OU2 in the root of the domain. Two Group Policy objects (GPOs) named GPO1 and GP02 are created. GPO1 is linked to OU1. GPO2 is linked to OU2. OU1 contains a client computer named Computer1. OU2 contains a user named User1.
You need to ensure that the GPOs Applied to Computer1 are Applied to User1 when User1 logs on.
What should you configure?
A. The GPO Status
B. WMI Filtering
C. GPO links
D. Security filtering
Answer: D
QUESTION 100
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2 and has the HyperV server role installed. On Server1, you create and start a virtual machine named VM1. VM1 is configured as shown in the following table.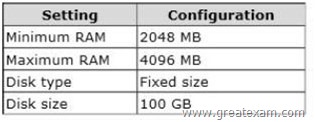
You plan to create a snapshot of VM1.
You need to recommend a solution to minimize the amount of disk space used for the snapshot of VM1.
What should you do before you create the snapshot?
A. Run the Stop-VM cmdlet.
B. Convert diskl.vhd to a dynamically expanding disk.
C. Configure VM1 to have a smaller virtual disk.
D. Decrease the Minimum RAM.
Answer: A
Explanation:
For checkpoints created when the virtual machine is stopped The checkpoint contains the state of the hard disks only. For checkpoints created when the virtual machine is running The checkpoint contains the state of the hard disks and the data in memory.
Note: A checkpoint saves the state of each virtual hard disk that is attached to a virtual machine and all of the hard disk’s contents, including application data files. For virtual machines on Hyper-V and VMware ESX Server hosts, a checkpoint also saves the hardware configuration information. By creating checkpoints for a virtual machine, you can restore the virtual machine to a previous state.
The Microsoft 70-417 questions and answers from GreatExam are the most reliable guide for Microsoft exam. We offer the latest 70-417 PDF and VCE dumps with new version VCE player for free download, and the newest 70-417 practice test ensures your exam 100% pass. A large number of successful candidates have shown a lot of faith in our 70-417 exam dumps. If you want pass the Microsoft 70-417 exam, please choose GreatExam.