In recent years, many people choose to take Microsoft 70-417 certification exam which can make you get the Microsoft certificate and that is the passport to get a better job and get promotions. How to prepare for Microsoft 70-417 exam and get the certificate? Please refer to Microsoft 70-417 exam questions and answers on GreatExam.
QUESTION 541
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
On all server computers Windows Server 2012 R2 is installed. All client computers Windows 8 is installed.
The domain comprises no certification authority (CA).
You must add in the domain a data recovery agent for the Encrypting File System (EFS). Which two steps you will perform? (Each correct answer presents part of the solution. Choose two.)
A. Run on the Windows PowerShell cmdlet Get-Certificate from.
B. Open the Default Domain Controllers Policy and perform the action data recovery agents create from.
C. Open the Default Domain Policy and perform the action data recovery agents to add from.
D. Run from the command prompt, the command-line utility Cipher.exe from
E. Open the Default Domain Policy, and perform the action data recovery agents create from.
F. Open the Default Domain Controllers Policy and perform the action data recovery agents to add from.
Answer: CD
Explanation:
With the call Cipher.exe/R:DRA we can create a certificate for EFS recovery. The command call creates a PFX file that contains the certificate and private key and a .CER file that contains only the certificate.
Then, the contents of the .cer file to the EFS recovery policy can be added to create the recovery key for users , The PFX file can be imported to restore individual files.
QUESTION 542
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
On all server computers Windows Server 2012 R2 is installed. All client computers Windows 8 is running.
You must control access to removable storage devices.
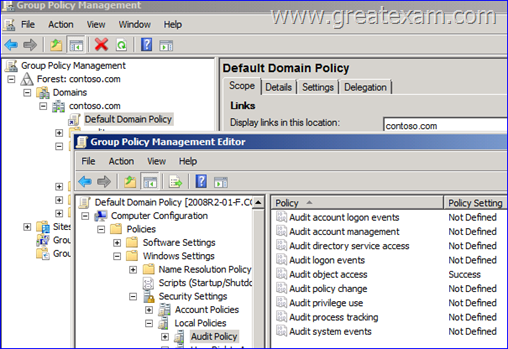
Which category you will configure? (To be configured dialog box shown in the picture. Click the Drawing button.)
A. Account Application
B. Account Management
C. DS Access
D. Object Access
E. Authorizations
F. System
Answer: D
Explanation:
What events in detail are affected by the audit policies, can be determined easily by a look at the subcategories of the expanded audit policy:
QUESTION 543
Your corporate network includes an Active Directory Domain Services (AD DS) domain named contoso.com .
The domain contains a Windows Server 2012 R2 computer that is named Server1. On Server1 the role Windows Server Update Services is installed.
You have created a new Group Policy object (GPO).
To configure the Windows Update settings of the client computer so that Windows updates are every Wednesday installed at 13:00 clock.
Which policy will configure? (To be configured dialog box shown in the picture. Click the Drawing button.)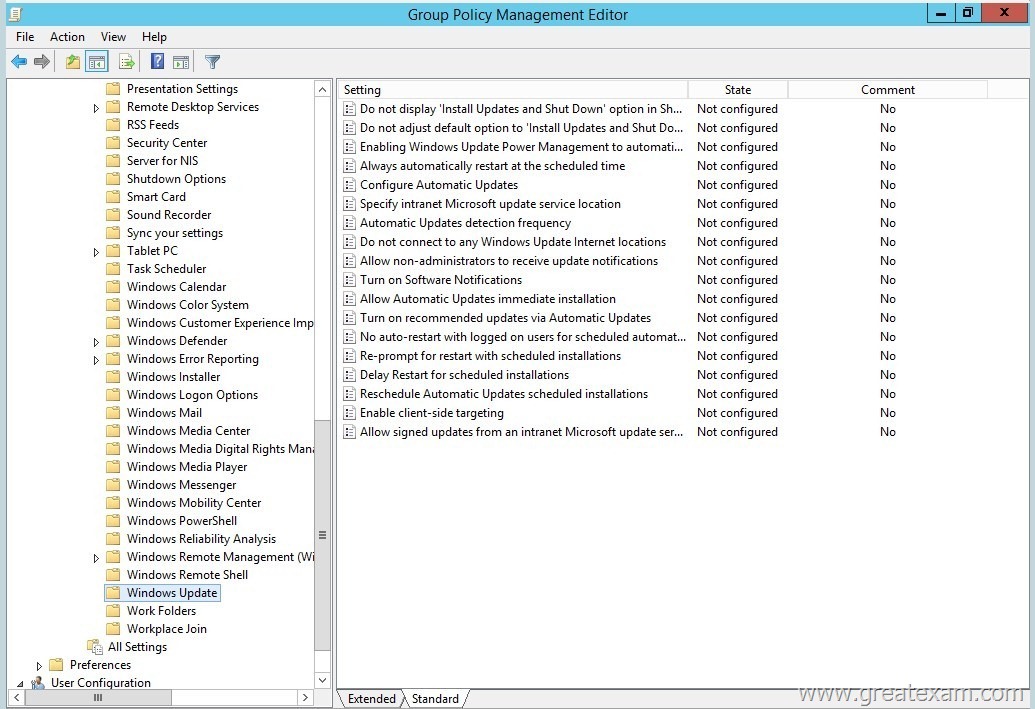
A. Configure Automatic Updates
B. Enable Client-side target allocation
C. Specify intranet Microsoft update service
D. Not allow administrators to receive update notifications
E. Enable Windows Update Power Management to reactivate the system to install scheduled updates automatically
F. Create new schedule of planned installations
Answer: A
Explanation:
The policy Configure Automatic Updates determines whether the computer security updates and other important downloads obtained via the Windows Automatic Updates service. In addition, you can specify one of the following options and a timetable for the installation:
2 = notify before downloading any updates and notify again before installation. If Windows detects updates that can be applied to the computer, an icon in the status area with a message that informs you that updates are available for download. Clicking the icon or message, you can select to download updates. The selected updates are then downloaded from Windows in the background. After downloading is complete, an icon in the status area again displayed that informs you that the updates can be installed. When you click the icon or message, you can select the updates that you want to install.
Automatically download 3 = (default) updates and notify you of updates installable Windows checks for updates that can be applied to the computer, and loads these automatically in the background without (the user is not notified during the process or disturbed). After downloading has been completed, the status area, the icon is displayed, informing you that the updates can be installed. When you click the icon or message, you can select the updates that you want to install.
Automatically download 4 = Updates and schedule that I specify install Specify the schedule using the options in the Group Policy setting. By default installations are planned daily for 3 clock in the morning, if no timetable is given. The completion of the update installation, if a restart is required, Windows will automatically restart the computer. (If a user is logged on to the computer when Windows is restarted, the user is notified and can delay the restart.)
5 = places allow administrators to select the configuration mode for the update installation through Automatic Updates This option can be enabled with local administrators, on the Control Panel icon “Automatic Updates” option to select a configuration. You can select a date for a planned installation example itself. Local administrators will not be allowed to disable the configuration for “Automatic Updates”.
QUESTION 544
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
On all server computers Windows Server 2012 R2 is installed.
The domain contains an organizational unit (OU) named CBDateiserver.
The OU contains the computer accounts of all file servers in the domain.
You need to monitor successful user access to file sharing, file server.
Which audit policy, you will configure?
(To be configured dialog box shown in the picture. Click the Drawing button.)
A. Audit logon events
B. Audit account logon events
C. Audit object access
D. Audit privilege use
E. Audit privilege use
F. Audit directory service access
Answer: C
Explanation:
With the security setting Audit object access is determined whether user access be monitored for non-Active Directory objects. Monitoring will be generated only for objects that is specified for its own SACL (System Access Control List, ACL on the system), and only then, if the requested access type (for example, write, read or modify) and the account from which the request originates, correspond to the settings in the SACL.
The administrator can specify whether only successful or failed only or both successful and unsuccessful operations, or basically no operations are monitored (ie neither successful nor unsuccessful operations).
If the monitoring of successful operations enabled is an audit entry for each successful access to a non-Active Directory object that has a matching SACL is indicated, is generated. If the monitoring of failed transactions is enabled, each time failed access to a non-Active Directory object for which a matching SACL specified, an audit entry is generated.
Note that you can set a SACL on an Active Directory object on the “Security” tab in the “Properties” of the object. Default:. No supervision order to gain more control over the audit policy, you can use the settings in the node “Advanced Audit Policy Configuration”.
QUESTION 545
Your corporate network includes an Active Directory Domain Services (AD DS) domain named contoso.com .
The domain contains a Windows Server 2012 R2 computer that is named Server1.
On Server1 the role Windows Server Update Services is installed.
You want to use a Group Policy object (GPO) to assign members of a computer group.
Which settings you will configure?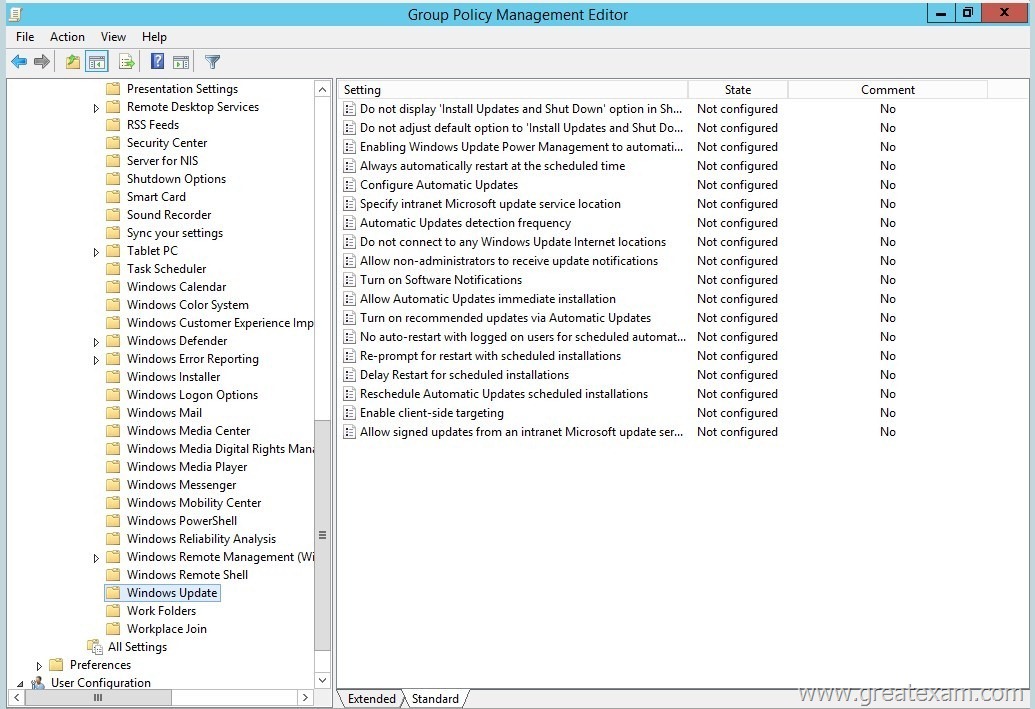
A. Configure Automatic Updates
B. Specify intranet Microsoft update service
C. Enable Software Notifications
D. Enable recommended updates via Automatic Updates
E. Enable Client-side targeting
F. Allow signed updates from an intranet Microsoft update service location
Answer: E
Explanation:
Computer can either manually or using the policy setting Client-side target association enable to computer groups of the Windows Server Update Services can be added.
The Directive Enable Client-side target mapping indicates the target group name or the name that will be used to receive updates from Microsoft Update Service on the intranet .
If the status to “Enabled” is set, the specified target group information to the Microsoft Update service will be sent on the intranet. This uses this information to determine which updates will be made available on the computer.
If the Microsoft update service location on the intranet supports multiple audiences, multiple, semicolon-separated group names can be specified by this Directive. Otherwise, a single group must be specified.
If the status is set to “Disabled” or “Not Configured”, no target group information to the Microsoft Update service will be sent on the intranet.
Note:
This policy applies only when the Microsoft Update service on the intranet, which this Computer use is configured to support client-side target allocation.
This policy has no effect when the policy is “intranet specify for Microsoft update service location” is disabled or not configured.
This policy is not supported on Windows RT. Enabling this policy on PCs running Windows RT runs has no effect.
QUESTION 546
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
On all domain controllers running Windows Server 2012 R2 is installed.
A support technician installed at an outdoor location Windows Server 2012 R2 on a server named DC10.
DC10 is currently a member of a workgroup.
You plan DC10 to a read-only domain controller (RODC) to change or “elevate”.
You must ensure that a user can promoted to a read-only domain controller with the username contoso \Tom DC10.
Your solution must the permissions that are granted to Tom, minimize.
How do you proceed?
A. Use the command-line tool Ntdsutil.exe and run the command Local Roles from.
B. Use Active Directory Users and Computers and create an account for a read-only domain controller.
C. Use the console Active Directory Users and Computers, and then run the wizard for assigning object management for container Domain Controllers from.
D. Take DC10 to the domain. And you change the properties of the computer account of DC10.
Answer: B
Explanation:
Use the context menu of the container domain controller you can access an assistant for a preliminary deployment of an account for a read-only domain controller. The wizard asks the name of the RODC, the destination site and the user account of a person from whom the permissions are delegated to install the read-only domain controller. The figure shows the relevant page of the wizard:
QUESTION 547
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
All servers running Windows Server 2012 R2 is installed.
The domain contains a server named Server1. On Server1 the role Windows Deployment Services Windows Deployment Services (WDS) installed.
You have received a list of MAC addresses newly purchased client computers.
You want the command-line utility wdsutil.exe use to provide in advance the new client computers in Active Directory.
What parameters do you use?
A. /get-AutoAddDevices
B. /get-Device
C. /add-Device
D. /enable
Answer: C
Explanation:
The /add-Device parameter allows the prerelease deployment of computer accounts in Active Directory for the installation of the Windows Deployment Services. The parameter allows you to configure all options that are possible when using the wizard, the console Windows Deployment Services.
The following call adds the Windows Deployment Services is a prerelease deployment for the computer Desktop1 with the MAC address 00-B0-56-88-2F -DC without giving added another option:
WDSUTIL /Add-Device /Device:Desktop1 /ID:00-B0-56-88-2F-DC
QUESTION 548
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
All servers running Windows Server 2012 R2 is installed.
The domain contains a server named Server1. On Server1 the role Windows Deployment Services Windows Deployment Services (WDS) installed.
You want the command-line utility wdsutil.exe use to retrieve information about the Active Directory provided in advance computer Desktop1.
What parameters do you use?
A. /get-AutoAddDevices
B. /get-Device
C. /add-Device
D. /enable
Answer: B
Explanation:
The / Get-Device parameters enables the retrieval of information on one or more devices prestaged. The following call retrieves information for a preliminary deployment of the computer Desktop2:
WDSUTIL / Get-Device / Device: Desktop2
QUESTION 549
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
The domain contains a domain controller that is named DC-1.
You run the command ping dc-1.contoso.local and get the command output shown in the picture (click on the button drawing).
You must ensure that DC-1 responds to a ping. What usually open in the Windows Firewall on DC-1? (This to configure dialog box is shown in the picture. Click the Drawing button.)
A. Active Directory Domain Controller – Echo Request (ICMPv4-In)
B. Active Directory Domain Controller – Echo Request (ICMPv6-In)
C. Active Directory Domain Controller – NetBIOS name resolution (UDP-In)
D. Core network – Destination Unreachable (ICMPv6-In)
E. Core network – Destination Unreachable, fragmentation required (ICMPv4-In)
F. Online Responder Service (DCOM-In)
Answer: A
Explanation:
The inbound rule “Active Directory Domain Controller – Echo Request (ICMPv4-In)” determines whether incoming ping requests to allow or block.
QUESTION 550
Your company uses an Active Directory Domain Services (AD DS) domain certbase.de named. The domain contains a server named Server1. On Server1 Windows Server 2012 R2 Standard is installed on a Server Core installation.
You need to ensure that Server1 on Windows Server 2012 R2 Datacenter is run in a Server Core installation.
You want to reach your destination with minimal administrative effort.
What do you do?
A. Perform a clean installation of Windows Server 2012 R2 on Server1.
B. Update the existing Windows Server 2012 R2 installation.
C. Use DISM and perform online maintenance.
D. Use DISM and perform an offline maintenance.
Answer: C
Explanation:
This command-line tool DISM.exe (Deployment Image Servicing and Management Tool) was introduced with Windows Server 2008 R2. In addition to numerous other ways can with DISM.exe also an in-place upgrade of Windows Server 2012 R2 Standard Windows Server performed 2012 R2 Datacenter be. The following command calls can be used here:
DISM / online / Get-Current Edition provides the Windows Edition currently used
DISM / online / Get-TargetEditions provides the possible upgrade paths
DISM / online / Set-Edition [ID Edition] / ProductKey: XXXXX-XXXXX-XXXXX-XXXXX-XXXXX
performs direct update by the specified edition.
QUESTION 551
You are working as a server administrator for the company CertBase.
To install Windows Server 2012 R2 Server Core on a new server computer that is named Server1.
Once you decide to install the graphical user interface (GUI) on Server1.
Which tool will you use?
A. PowerShell cmdlet Add-Windows Package
B. PowerShell Cmdlet Add-WindowsFeature
C. PowerShell Cmdlet Install-Module
D. PowerShell Cmdlet Install-RoleService
Answer: B
Explanation:
Among the new features of Windows Server 2012 and Windows Server 2012 R2 include the ability to install them separately or can remove the GUI after the initial installation. In the blog you can find more information on the topic:
QUESTION 552
You work as an administrator for the company Contoso.
You administer a Windows Server 2012 R2 computer that is named Server1.
You want to create an image of Server1.
To keep the size of the image as small as possible, you want to remove the source files of all server roles that are not installed on Server1.
Which tool you are use?
A. Ocsetup.exe
B. ServerManagerCMD.exe
C. ImageX.exe
D. Dism.exe
Answer: D
Explanation:
In order to limit the attack surface of a server to a minimum or to reduce the installation files for a scheduled imaging, you can completely remove the program files of roles and features that you are not using from the hard disk.
The cmdlet Uninstall Windows feature has for this purpose over the -Remove parameter. Alternatively, the command line program Dism.exe with the /Disable-Feature can be used. Dism.exe also has the new parameter /Cleanup-Image, which it experienced allows users the size of the directory WinSxS by removing unneeded components to reduce:
QUESTION 553
Your network includes five servers running the operating system Windows Server 2012 R2.
In the five servers, the Failover Clustering feature is installed.
To create a new cluster with the name Cluster1.
The configuration of the cluster is shown in the picture (click on the button drawing).
Site B is a site for disaster recovery.
Server1, Server2 and Server3 are configured as the preferred owner of Cluster1.
The dynamic quorum management is disabled.
You are planning a hardware maintenance for Server3.
You must make sure that the cluster resources remain available to Site A if the WAN connection fails while you are performing maintenance on Server3.
How do you proceed?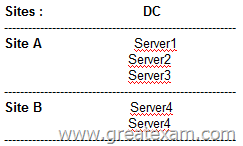
A. Create in StandortA a witness file share.
B. Remove Server3 the nodes vote.
C. Remove Server4 and Server5 the nodes vote.
D. Enable the dynamic quorum administration.
Answer: C
Explanation:
The quorum configuration in a failover cluster, the number of failures is determined that can be tolerated by the cluster. If another failure occurs, the cluster must stop running. The relevant in this context are failures or node failures – in some cases – failure of a witness disk (of a copy of the cluster configuration contains) or a witness file share.
It is essential that the cluster is no longer running, enter if too many failures, or if a problem with the communication between the cluster nodes is present.
In Windows Server 2012 and Windows Server 2012 R2, you can a node on the extended quorum settings the “right to vote “escape and manually influence the determination of the majorities in special situations.
https://technet.microsoft.com/en-us/library/jj612870.aspx
QUESTION 554
You are working as a server administrator for the company contoso.local.
They serve 30 servers on which the operating system is Windows Server 2012 R2 installed.
All servers are backed up daily by Windows Azure Online Backup.
You must perform on all servers an immediate backup in Windows Azure Online Backup.
What PowerShell cmdlets are on each server Run?
A. Start OBRegistration | Start OBBackup
B. Get-OBPolicy | Start OBBackup
C. Get-WBBackupTarget | Start WBBackup
D. Get-WBPolicy | Start WBBackup
Correct
Answer:
Explanation:
The cmdlet Start-OBBackup starts a one-time backup based on the direction indicated by the -Policy parameter settings.
The following example retrieves the backup settings and transfers them to the cmdlet Start-OBBackup:
Get-OBPolicy | Start OBBackup
Gives the following example the Directive explicitly named at:
Start-OBBackup -Name myPolicy
QUESTION 555
You are working as a server administrator for the company contoso.
They serve 20 servers on which the operating system is Windows Server 2012 R2 installed.
You must create a Windows PowerShell script that each server is registered in Windows Azure Online Backup.
In addition, the script must specify the encryption passphrase.
Which two PowerShell cmdlets, you will include in your script? (Each correct answer presents part of the solution. Choose two.)
A. New-OBPolicy
B. New-OBRetentionPolicy
C. Add-OBFileSpec
D. Start-OBRegistration
E. Set-OBMachineSetting
Answer: DE
Explanation:
When you register a server with Windows Azure Online Backup, creates a space allocation for the server in the cloud service, and the server is associated with the subscription. Each server whose elements you want to back up must be registered with the service, so that online backups can be performed. The initial configuration of Windows Azure Online Backup Agent is done by a server using the Windows Azure Online Backup Agent snap-in or Windows register PowerShell cmdlets for Windows Azure Online Backup Online Portal. Before registering a server for use with Windows Azure Online Backup, you must run the process described under Log for Windows Azure Online Backup and install Windows Azure Online Backup Agent.
You can register in 2012 every server running Windows Server 2012 and Windows Server R2, you want to protect. Prerequisite to perform this operation is a member of the local Administrators group or equivalent membership. The following code example demonstrates that you can register a server with Windows Azure Online Backup with Windows PowerShell after you have defined variables for providing the credentials. If no credentials are specified, you are prompted by the Registry cmdlet prior to registration, enter the account credentials for the user ID. However, they are not prompted for the additional server properties that you have configured using the wizard for registering servers. You can copy the sample code and paste it into a Windows
PowerShell script.
$pwd = ConvertTo-SecureString -String -AsPlainText –Force
$cred = New-Object –TypeName System.Management.Automation.PsCredential –ArgumentList , $pwd
Start-OBRegistration -Credential $cred
If the server is registered, you must specify the server properties with the set-OBMachineSetting cmdlet. In the following examples show how the various settings can be specified:
Specifying the encryption passphrase
$pass = ConvertTo-SecureString -String -AsPlainText –Force
Set-OBMachineSetting -EncryptionPassphrase $pass
Configuring proxy settings
$spwd = ConvertTo-SecureString -String -AsplainText –Force
Set-OBMachineSetting -ProxyServer proxycontoso.com -ProxyPort -ProxyUsername Domäne\Benutzername -ProxyPassword $spwd
Configuring throttling settings for bandwidth
$mon = [System.DayOfWeek]::Monday
$tue = [System.DayOfWeek]::Tuesday
Set-OBMachineSetting -WorkDay “Mo”, “Tu” -StartWorkHour “9:00:00” -EndWorkHour “18:00:00” -WorkHourBandwidth (512*1024) -NonWorkHourBandwidth (2048*1024)
If a server does not throttling settings to be used for more bandwidth, use the following command:
Set-OBMachineSetting -NoThrottle
QUESTION 556
Your company uses an Active Directory Domain Services (AD DS) domain named contos.local. On all servers in the network, the operating system is Windows Server 2012 R2 installed.
The domain contains a file server named Server1. On Server1 role service Resource Manager File Server is installed.
The computer account of Server1 is in an organizational unit (OU) named OU1.
You have a Group Policy object (GPO) created with the name GPO1 and linked it with OU1.
The relevant settings GPO1 are shown in the picture (click on the button drawing).
Server1 contains a folder named Data1. The folder is shared under the name documents1 the network. They are trying to “access denied” support according to Configure Server1.
However, you can change the settings for the support for “Access Denied” in the Resource Manager file server is not configured.
You must make sure that you “access denied” the settings for the support according to manually configure file servers on Server1 in Resource Manager.
How do you proceed?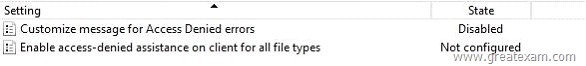
A. Enable the policy setting in GPO1 message for error type “Access Denied” adapt.
B. Activate in GPO1 the policy setting support for “Access Denied” Enable Client for all file types.
C. Configure the policy setting “Access Denied” message for error type adapt in GPO1 with Not Configured.
D. Disable GPO1 in the policy setting support for “Access Denied” Enable Client for all file types.
Answer: C
Explanation:
policy settings, see >> Computer Configuration \ Policies \ Administrative Templates \ System \ Access-denied-Assistance
message for error type “Access Denied” Customize With this Directive, the message indicates that users see when accessing a file or folder has been denied.
You can download the message of type “Access Denied” supplemented by additional text and links. Moreover, you can offer users the ability to send an email to request access to the file or folder, or the access is denied for.
If you enable this policy setting, users will receive a custom message type “Access denied” from the file servers on which this policy setting is enabled.
If you disable this policy setting, users with a default message type “Access Denied” is displayed, which provides, irrespective of the file server configuration none of the controlled by this policy setting functions.
If this do not configure policy setting, users will be a default message “Access Denied” type appears, unless the file server was configured to the user-defined message is displayed.
By default, users will get the default message “Access Denied” type displayed. Support “Access Denied” by Enable Client for all file types, this policy setting should be set to Windows clients to the support for “Access Denied” to activate for all file types.
QUESTION 557
You are working as a network administrator for the company contoso.
Your network includes a Windows Server 2012 R2 computer that is named Server1.
To install the role file / storage services on Server1.
You use the Windows Explorer and open the properties of a folder named documents1.
They note that the register classification is missing.
You must ensure that you can use Windows Explorer to assign the folder manually documents1 classifications.
How do you proceed?
A. Configure the Folder Options and uncheck the option (Recommended) Sharing Wizard.
B. Install the role service Resource Manager file server.
C. Configure the Folder Options and uncheck Hide protected operating system files (Recommended).
D. Install the Role Management Tool tools for sharing and Memory management.
Answer: B
Explanation:
The Resource Manager
File Server provides a number of features for managing and classifying data stored on file servers data. The Resource Manager File Server includes the following features:
File Classification Infrastructure Provides an insight into your data, which facilitate more efficient data management is made possible by automating classification processes. You can classify files and apply policies based on this classification. Example policies include dynamic access control for restricting file access, file encryption and file expiration. Files can be automatically classified based on file classification rules or manually by changing the properties of a selected file or folder.
File Management Tasks
Apply a conditional policy or action for files based on their classification. Among the conditions of a file management task include the file location, the classification properties, the creation date of the file, the date the file was last modified or the date the file was last accessed. Among the possible actions for a file management task includes the ability to run off of files, to encrypt files or to execute a custom command.
Quota Management
Limit the allowed for a volume or folder location, and can be automatically applied to new folders that are created on a volume. You can also define quota templates that can be applied to new volumes or folders.
File Screening Management
Controls the types of files that users can save on a file server. You can restrict the extensions that can be stored on the file share. For example you can create a file screen, which prevents files are saved with the extension MP3 in personal shared folders on a file server.
Storage Reports
Identify trends in disk usage and the way in which the data are classified. Storage Reports also monitor attempts to selected user groups to save unauthorized files.
The features of the File Server Resource Manager can be configured and managed with the MMC Resource Manager File Server or with Windows PowerShell.
QUESTION 558
Your corporate network includes an Active Directory Domain Services (AD DS) domain named contoso. The domain contains a Windows Server 2012 R2 member server named Server1.
On Server1 role service Resource Manager is installed on the file server.
You need to configure Server1 to the following requirements:
– Old files that are located in a folder named Folder1, must be moved to
a folder named Archiv1.
– All reports must be stored in a network share.
Which two nodes need to Configure? (To be configured dialog box shown in the picture. Click the Drawing button.)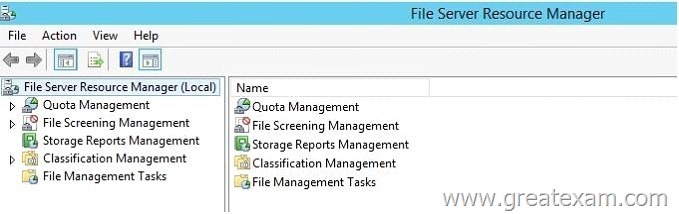
A. Resource Manager File Server (locally)
B. Quotas
C. File Screens
D. Storage Reports Management
E. Classification rules
F. File management tasks
Answer: AF
Explanation:
For moving old files a file management task can be type file sequence are created.
The locations for reports on the roster report locations are configured in the Options for the Resource Manager file server. By default, the reports are stored in a local directory.
QUESTION 559
You are working as a server administrator for the company Contoso.
You administer a Windows Server 2012 R2 Server Core computer named Server1.
Server1 is used as a file server.
You must ensure that users register previous versions can use to access previous versions of files.
Which tool will you use?
A. Wbadmin
B. Diskpart
C. Storrept
D. Vssadmin
Answer: D
Explanation:
With previous versions, you can access previous versions of files and folders that are shared on your network. This can be accessed on previous versions of files, must “Shadow Copies of Shared Folders” is enabled on the file server. Previous versions are read-only until the restoration. A previous version of the file on the server can not be changed. Calling an earlier version of a file
Locate the file (on the network), from which you want to view an earlier version, you click with the right mouse button, and select Properties.
On the Previous Versions tab, select the desired version, and click Open.
In a full installation of Windows Server 2012 R2, you can enable earlier versions of the properties of the volume.
A Server Core version, you can use the administrative command-line tool of the Volume Shadow Copy Service (Vssadmin). To enable Shadow Copies of Volume D and to save on volume E example, you can run the following command:
Vssadmin Add ShadowStorage /for=d: /on=e: /maxsize=2GB
QUESTION 560
Your corporate network includes two Active Directory Domain Services (AD DS) domains. contoso.com The names of the domains loud and traincert.com.
You administer a Windows Server 2012 R2 computer that is named Server1.
On Server1, the DNS server role is installed.
The server hosting a copy of the zone contoso.com.
You need to configure Server1 traincert.de for the resolution of the name of the zone.
Your solution must meet the following requirements:
– It must be avoided that the configuration of the name servers of the
zone traincert.de must be adapted when it changes.
– The administrative expenses for the maintenance and care of your
solution should turn out as low as possible.
What type of zone you are using?
A. A primary zone
B. A secondary zone
C. A reverse lookup zone
D. A stub zone
Answer: D
Explanation:
Stub zones contain only name server records (NS) and its host (A) records. The DNS client can retrieve a list of authorized name servers on the stub zone. The host changes (A) entry of a name server is a stub zone (as opposed to a delegated zone) automatically updated. There are no manual steps to adapt the Domain Name System (DNS) is required.
GreatExam is a good website that provides all candidates with the latest IT certification exam materials. GreatExam will provide you with the exam questions and verified answers that reflect the actual exam. The Microsoft 70-417 exam dumps are developed by experienced IT professionals. 99.9% of hit rate. Guarantee you success in your 70-417 exam with our exam materials.