GreatExam dumps for 70-410 exam are written to the highest standards of technical accuracy, provided by our certified subject matter experts and published authors for development. We guarantee the best quality and accuracy of our products. We hope you pass the exams successfully with our practice test. With our Microsoft 70-410 practice test, you will pass your exam easily at the first attempt. You can also enjoy 365 days free update for your product.
QUESTION 311
Your network contains two Active Directory forests named contoso.com and adatum.com. Each forest contains one domain. A two-way forest trust exists between the forests.
The forests use the address spaces shown in the following table.

From a computer in the contoso.com domain, you can perform reverse lookups for the servers in the contoso.com domain, but you cannot perform reverse lookups for the servers in the adatum.com domain. From a computer in the adatum.com domain, you can perform reverse lookups for the servers in both domains.
You need to ensure that you can perform reverse lookups for the servers in the adatum.com domain from the computers in the contoso.com domain.
What should you create?
A. a delegation
B. a trust point
C. a conditional forwarder
D. a GlobalNames zone
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc757172(v=ws.10).aspx
Conditional forwarders are DNS servers that only forward queries for specific domain names. Instead of forwarding all queries it cannot resolve locally to a forwarder, a conditional forwarder is configured to forward a query to specific forwarders based on the domain name contained in the query. Forwarding according to domain names improves conventional forwarding by adding a name-based condition to the forwarding process.
The conditional forwarder setting for a DNS server consists of the following:
The domain names for which the DNS server will forward queries.
One or more DNS server IP addresses for each domain name specified.
When a DNS client or server performs a query operation against a DNS server, the DNS server looks to see if the query can be resolved using its own zone data or the data stored in its cache. If the DNS server is configured to forward for the domain name designated in the query, then the query is forwarded to the IP address of a forwarder associated with the domain name. For example, in the following figure, each of the queries for the domain names is forwarded to a DNS server associated with the domain name.
QUESTION 312
Your network contains an Active Directory domain named contoso.com.
The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Server2 establishes an IPSec connection to Server1.
You need to view which authentication method was used to establish the initial IPSec connection. What should you do?
A. From Windows Firewall with Advanced Security, view the quick mode security association.
B. From Event Viewer, search the Application Log for events that have an ID of 1704.
C. From Event Viewer, search the Security Log for events that have an ID of 4672.
D. From Windows Firewall with Advanced Security, view the main mode security association.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/dd448497(v=ws.10).aspx
Main mode negotiation establishes a secure channel between two computers by determining a set of cryptographic protection suites, exchanging keying material to establish a shared secret key, and authenticating computer and user identities. A security association (SA) is the information maintained about that secure channel on the local computer so that it can use the information for future network traffic to the remote computer.
You can monitor main mode SAs for information like which peers are currently connected to this computer and which protection suite was used to form the SA.
To get to this view
In the Windows Firewall with Advanced Security MMC snap-in, expand Monitoring, expand Security Associations, and then click Main Mode.
The following information is available in the table view of all main mode SAs. To see the information for a single main mode SA, double-click the SA in the list.
Main mode SA information
You can add, remove, reorder, and sort by these columns in the Results pane:
Local Address: The local computer IP address.
Remote Address: The remote computer or peer IP address.
1st Authentication Method: The authentication method used to create the SA.
1st Authentication Local ID:: The authenticated identity of the local computer used in first authentication.
1st Authentication Remote ID: The authenticated identity of the remote computer used in first authentication.
2nd Authentication Method: The authentication method used in the SA.
2nd Authentication Local ID:: The authenticated identity of the local computer used in second authentication.
2nd Authentication Remote ID: The authenticated identity of the remote computer used in second authentication.
Encryption: The encryption method used by the SA to secure quick mode key exchanges.
Integrity: The data integrity method used by the SA to secure quick mode key exchanges.
Key Exchange: The Diffie-Hellman group used to create the main mode SA.
QUESTION 313
Hotspot Question
You have a Group Policy object (GPO) named Server Audit Policy.
The settings of the GPO are shown in the Settings exhibit. (Click the Exhibit button.)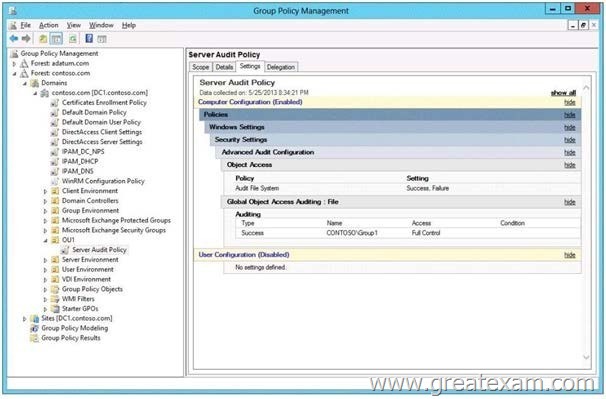
The scope of the GPO is shown in the Scope exhibit. (Click the Exhibit button.)
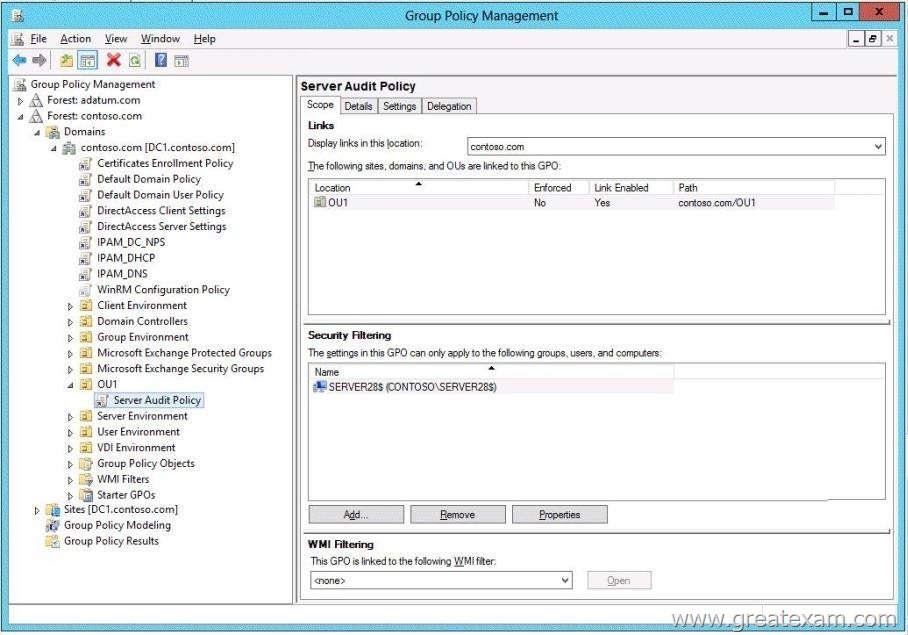
The domain contains a group named Group1. The membership of Group1 is shown in the Group1 exhibit. (Click the Exhibit button.)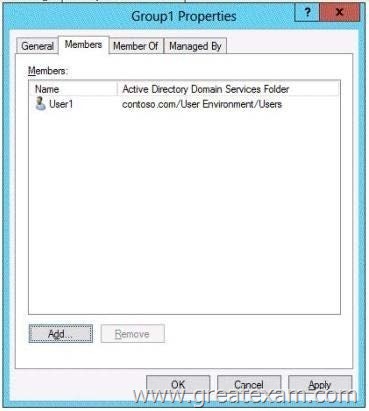
Select Yes if the statement can be shown to be true based on the available information; otherwise select No. Each correct selection is worth one point.
Answer: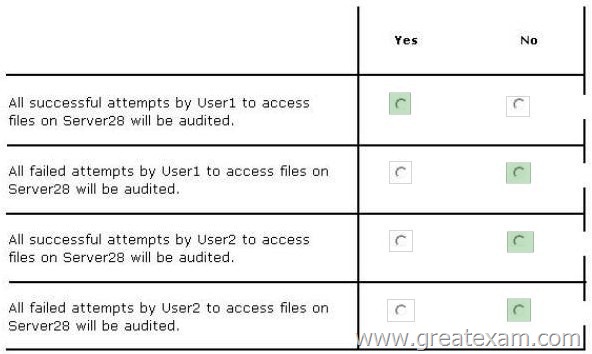
QUESTION 314
Your network contains an Active Directory domain named contoso.com. The domain contains an Application server named Server1. Server1 runs Windows Server 2012 R2. Server1 is configured as an FTP server. Client computers use an FTP Application named App1.exe. App1.exe uses TCP port 21 as the control port and dynamically requests a data port. On Server1, you create a firewall rule to allow connections on TCP port 21. You need to configure Server1 to support the client connections from App1.exe. What should you do?
A. Run netshadvfirewall set global statefulftp enable.
B. Create an inbound firewall rule to allow App1.exe.
C. Create a tunnel connection security rule.
D. Run Set-NetFirewallRule -DisplayNameDynamicFTP -Profile Domain
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc771920%28v=ws.10%29.aspx#BKMK_set_2a
The netsh firewall context is supplied only for backward compatibility. We recommend that you do not use this context on a computer that is running Windows Vista or a later version of Windows
In the netsh advfirewall firewall context, the add command only has one variation, the add rule command.
Netsh advfirewall set global statefulftp:
Configures how Windows Firewall with Advanced Security handles FTP traffic that uses an initial connection on one port to request a data connection on a different port.
When statefulftp is enabled, the firewall examines the PORT and PASV requests for these other port numbers and then allows the corresponding data connection to the port number that was requested.
Syntax
set global statefulftp { enable | disable | notconfigured }
Parameters
statefulftp can be set to one of the following values:
enable
The firewall tracks the port numbers specified in PORT command requests and in the responses to PASV requests, and then allows the incoming FTP data traffic entering on the requested port number.
disable
This is the default value. The firewall does not track outgoing PORT commands or PASV responses, and so incoming data connections on the PORT or PASV requested port is blocked as an unsolicited incoming connection.
notconfigured
Valid only when netsh is configuring a GPO by using the set store command.
QUESTION 315
Your network contains an Active Directory domain named contoso.com.
You have a Group Policy object (GPO) named GPO1 that contains several user settings. GPO1 is linked to an organizational unit (OU) named OU1.
The help desk reports that GPO1 Applies to only some of the users in OU1.
You open Group Policy Management as shown in the exhibit. (Click the Exhibit button.)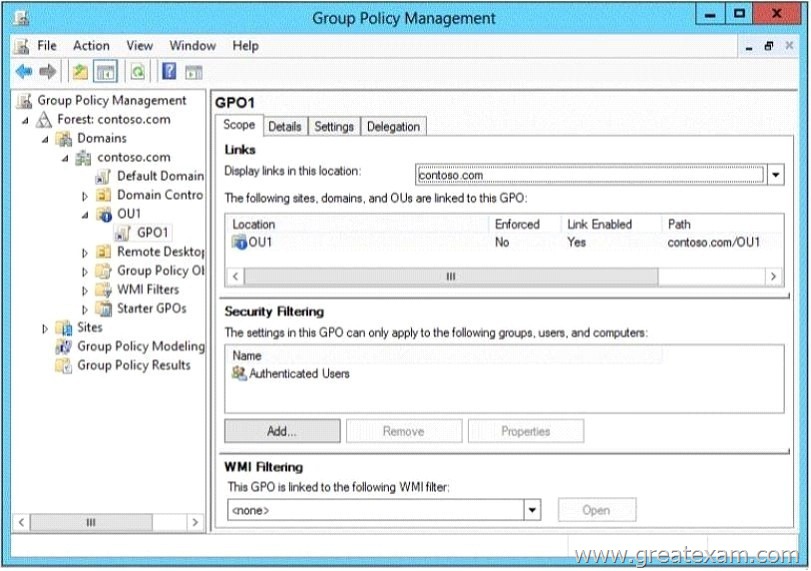
You need to configure GPO1 to Apply to all of the users in OU1.
What should you do?
A. Modify the Security settings of GPO1.
B. Disable Block Inheritance on OU1.
C. Modify the GPO status of GPO1.
D. Enforce GPO1.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc739343(v=ws.10).aspx
QUESTION 316
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have configured a server, named L2P-SR07, as a VPN server.
You are required to configure new firewall rules for workstation connections.
You want to achieve this using the least amount of administrative effort.
Which of the following actions should you take?
A. You should consider making use of the Enable-NetFirewallRule cmdlet.
B. You should consider making use of the New-NetFirewallRule cmdlet.
C. You should consider making use of dism.exe from the command prompt.
D. You should consider making use of dsadd.exe from the command prompt.
Answer: B
Explanation:
New-NetFirewallRule – Creates a new inbound or outbound firewall rule and adds the rule to the target computer.
You can’t Enable what doesn’t exist yet… you must use New-NetFirewallRule
http://technet.microsoft.com/en-us/library/jj554908%28v=wps.620%29.aspx http://blogs.technet.com/b/heyscriptingguy/archive/2012/11/13/use-powershell-to-create-new-windows-firewall-rules.aspx
QUESTION 317
Hotspot Question
Your company has a main office and a sales office. The main office has 2,000 users.
The sales office has 20 users. All client computers in the sales office run Windows 8. The sales office contains a print server named App1 that runs Windows Server 2012 R2.
App1 has a shared printer named Printer1. Printer1 connects to a network-attached print device.
You plan to connect all of the users in the sales office to Printer1 on App1.
You need to ensure that if App1 fails, the users can continue to print to Printer1.
What should you configure on App1? To answer, select the appropriate option in the answer area.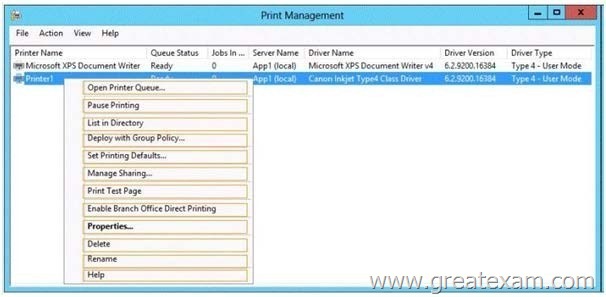
Answer: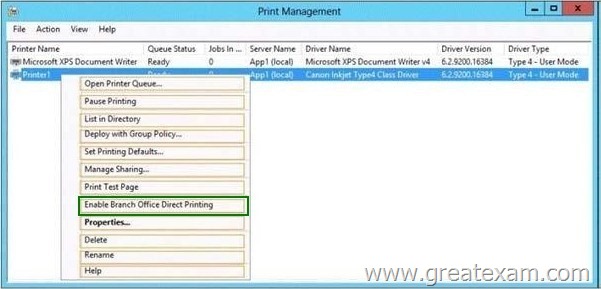
QUESTION 318
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 and has the HyperV server role installed. On Server1, an administrator creates a virtual machine named VM1. A user named User1 is the member of the local Administrators group on Server1. User1 attempts to modify the settings of VM1 as shown in the following exhibit. (Click the Exhibit button.)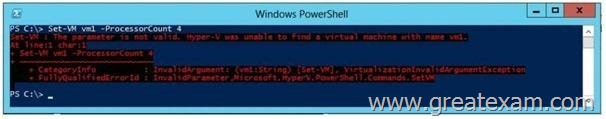
You need to ensure that User1 can modify the settings of VM1 by running the Set-Vm cmdlet.
What should you instruct User1 to do?
A. Import the Hyper-V module.
B. Install the Integration Services on VM1.
C. Run Windows PowerShell with elevated privileges.
D. Modify the membership of the local Hyper-V Administrators group.
Answer: C
Explanation:
You can only use the PowerShell snap-in to modify the VM settings with the vmcmdlets when you are an Administrator.
Thus best practices dictate that User1 run the Powershell with elevated privileges.
http://technet.microsoft.com/en-us/library/jj713439.aspx
QUESTION 319
Drag and Drop Question
You have a Hyper-V host named Server1. A technician creates a virtual machine named VM1 on Server1 by using the New Virtual Machine Wizard.
You start VM1 and you discover that there is no option to start by using PXE.
You need to ensure that you can start VM1 by using PXE.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)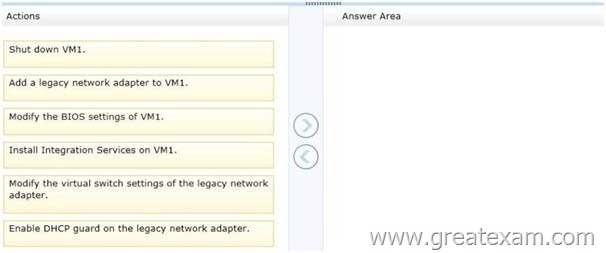
Answer: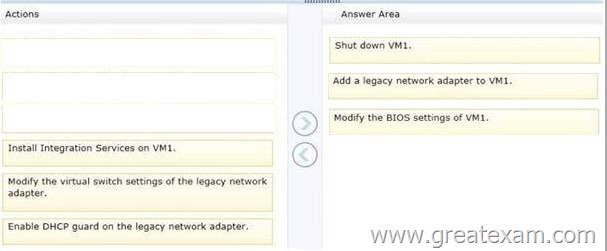
QUESTION 320
Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the HyperV server role installed.
You need to implement NIC teaming on Server1.
Which two network connections should you include on the NIC team? (To answer, select the two appropriate network connections in the answer area.)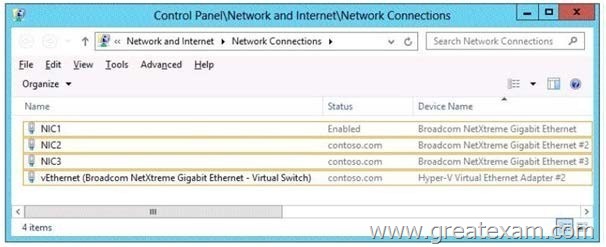
Answer: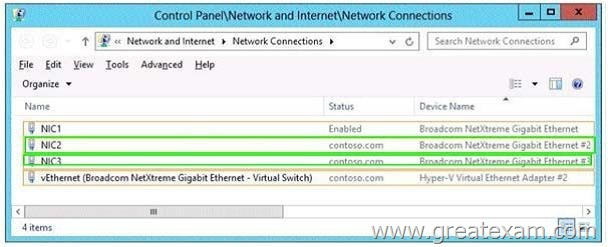
QUESTION 321
You have 3 server named Server1. Server1 runs a Server Core installation of Windows Server 2012 R2. The local area connection on Server1 has the following configuration:
IP address: 10.1.1.1
– Subnet mask: 255.255.240.0
– Default gateway: 10.1.1.254
– Preferred DNS server: <none>
The network contains a DNS server that has an IPv4 address of 10.1.1.200.
You need to configure Server1 to use 10.1.1.200 as the preferred DNS server.
The solution must not change any other settings on Server1.
Which command should you run?
A. sconfig.cmd
B. net.exe
C. Set-NetIPInterface
D. netsh.exe
Answer: A
Explanation:
In Windows Server 2012 R2, you can use the Server Configuration tool (Sconfig.cmd) to configure and manage several common aspects of Server Core installations. Network settings You can configure the IP address to be assigned automatically by a DHCP Server or you can assign a static IP address manually. This option allows you to configure DNS Server settings for the server as well.
Sconfig.cmd interface
QUESTION 322
You have a server named Server1 that runs Windows Server 2012 R2.
On Server1, you open Computer Management as shown in the exhibit. (Click the Exhibit button.)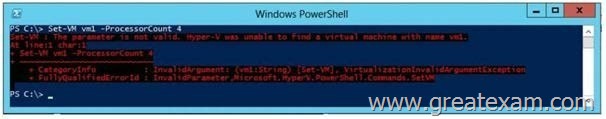
You need to ensure that you can create a 3-TB volume on Disk 1. What should you do first?
A. Create a storage pool.
B. Convert the disk to a GPT disk.
C. Create a VHD, and then attach the VHD.
D. Convert the disk to a dynamic disk.
Answer: B
Explanation:
The exhibit shows Disk1 to be a basic disk.
The disk must be GPT since GPT disks allows for partitioning.
http://msdn.microsoft.com/en-us/library/windows/hardware/gg463525.aspx
QUESTION 323
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
L2P.com has a domain controller, named L2P-DC01.
You have been instructed to make sure that the Group Policy Administrative Templates are available centrally.
Which of the following actions should you take?
A. You should consider copying the policies folder to the PolicyDefinitions folder in the L2P.com
domain’s SYSVOL folder.
B. You should consider copying the PolicyDefinitions folder to the policies folder in the L2P.com
domain’s SYSVOL folder.
C. You should consider copying the PolicyDefinitions folder to the policies folder in the L2P.com
domain’s systemroot folder.
D. You should consider copying the PolicyDefinitions folder to the policies folder in the L2P.com
domain’s logonserver folder.
Answer: B
Explanation:
PolicyDefinitions folder within the SYSVOL folder hierarchy. By placing the ADMX files in this directory, they are replicated to every DC in the domain; by extension, the ADMX-aware Group Policy Management Console in Windows Vista, Windows 7, Windows Server 2008 and R2 can check this folder as an additional source of ADMX files, and will report them accordingly when setting your policies.
By default, the folder is not created. Whether you are a single DC or several thousand, I would strongly recommend you create a Central Store and start using it for all your ADMX file storage. It really does work well.
The Central Store To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder on a domain controller. The Central Store is a file location that is checked by the Group Policy tools. The Group Policy tools use any .admx files that are in the Central Store. The files that are in the Central Store are later replicated to all domain controllers in the domain.
To create a Central Store for .admx and .adml files, create a folder that is named PolicyDefinitions in the following location: \\FQDN\SYSVOL\FQDN\policies
Note: FQDN is a fully qualified domain name.
http://tigermatt.wordpress.com/tag/policydefinitions/
http://support.microsoft.com/kb/929841/en-us
http://www.virtuallyimpossible.co.uk/how-to-create-a-group-policy-central-store/ http://support.microsoft.com/kb/2741591/en-us
QUESTION 324
Your network contains an Active Directory domain named contoso.com. The password policy for the domain is set to require a minimum password length of 10 characters. A user named User1 and a user named User2 work for the sales department. User1 is forced to create a domain password that has a minimum of 12 characters.
User2 is forced to create a domain password that has a minimum of eight characters.
You need to identify what forces the two users to have different password lengths.
Which tool should you use?
A. Credential Manager
B. Security Configuration Wizard (SCW)
C. Group Policy Management
D. Active Directory Administrative Center
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc770842(v=ws.10).aspx
In Windows Server 2008, you can use fine-grained password policies to specify multiple password policies and apply different password restrictions and account lockout policies to different sets of users within a single domain. For example, to increase the security of privileged accounts, you can apply stricter settings to the privileged accounts and then apply less strict settings to the accounts of other users. Or in some cases, you may want to apply a special password policy for accounts whose passwords are synchronized with other data sources.
QUESTION 325
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
L2P.com has a Hyper-V server, named L2P-SR13, which hosts multiple virtual machines.
You have enabled the use of Single-root I/O virtualization.
Which of the following is TRUE with regards to using Single-root I/O virtualization? (Choose all that apply.)
A. It maximizes network throughput, while minimizing network latency.
B. It maximizes network throughput, as well as network latency.
C. It avoids the virtual switch stack and allows the virtual machine direct access to the actual network switch.
D. It prevents the virtual machine from accessing the network switch directly.
Answer: AC
Explanation:
SR-IOV enables network traffic to bypass the software switch layer of the Hyper-V
virtualizationstack. Because the VF is assigned to a child partition, the network traffic flows directly between the VF and child partition. As a result, the I/O overhead in the software emulation layer is diminished and achieves network performance that is nearly the same performance as in nonvirtualized environments.
http://msdn.microsoft.com/en-us/library/windows/hardware/hh440148%28v=vs.85%29.aspx
QUESTION 326
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators.
You are currently discussing the use of Non-Uniform Memory Architecture (NUMA).
Which of the following is TRUE with regards to Non-Uniform Memory Architecture (NUMA)? (Choose two.)
A. It is a computer architecture used in multiprocessor systems.
B. It is a computer architecture used in single processor systems.
C. It allows a processor to access local memory faster than it can access remote memory.
D. It allows a processor to access remote memory faster than it can access local memory.
Answer: AC
Explanation:
NUMA is a hardware design feature that divides CPUs and memory in a physical server into NUMA nodes. You get the best performance when a process uses memory and CPU from within the same NUMA node.
de is full, then it’ll get memory from
When a process requires more memory, but the current NUMA no
another NUMA node and that comes at a performance cost to that process, and possibly all other processes on that physical server.
And that’s why virtualization engineers need to be aware of this. In Hyper-V we have Dynamic Memory.
Non-Uniform Memory Access or Non-Uniform Memory Architecture (NUMA) is a computer memory design used in multiprocessors, where the memory access time depends on the memory location relative to a processor. Under ccNUMA, a processor can access its own local memory faster than non-local memory, that is, memory local to another processor or memory shared between processors. NUMA architectures logically follow in scaling from symmetric multiprocessing (SMP) architectures.
http://en.wikipedia.org/wiki/Non-Uniform_Memory_Access
http://www.aidanfinn.com/?p=11945
QUESTION 327
Hotspot Question
You have a server named DHCP1 that runs Windows Server 2012 R2. DHCP1 does not ave access to the Internet. All roles are removed completely from DHCP1.
You mount a Windows Server 2012 R2 installation image to the C:\Mount folder.
You need to install the DHCP Server server role on DHCP1 by using Server Manager.
Which folder should you specify as the alternate path for the source files? To answer, select the appropriate folder in the answer area.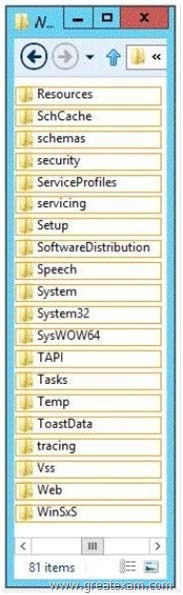
Answer: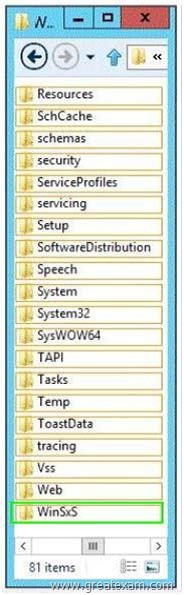
QUESTION 328
You have a server named Data1 that runs a Server Core Installation of Windows Server 2012 R2 Standard.
You need to configure Data1 to run a Server Core Installation of Windows Server 2012 R2 Enterprise.
You want to achieve this goal by using the minimum amount of administrative effort.
What should you perform?
A. a clean installation of Windows Server 2012
B. an offline servicing by using Dism
C. an online servicing by using Dism
D. an upgrade installation of Windows Server 2012
Answer: C
Explanation:
ROD: windows server 2012 enterprise DOES NOT EXIST, maybe they meant data center?
http://technet.microsoft.com/en-us/library/hh825157.aspx
QUESTION 329
You have a server named Server1 that runs Windows Server 2012 R2.
You need to enable access-based enumeration for a file share on Server1.
Which tool should you use?
A. File Server Resource Manager (FSRM)
B. File Explorer
C. Share and Storage Management
D. Server Manager
Answer: D
Explanation:
Windows 2008 use Share and Storage Management
Windows 2012 use Server Manager
QUESTION 330
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1. Server1 runs Windows Server 2012 R2.
You plan to create a shared folder. The shared folder will have a quota limit.
You discover that when you run the New Share Wizard, you cannot select the SMB Share – Advanced option.
You need to ensure that you can use SMB Share – Advanced to create the new share.
What should you do on Server1 before you run the New Share Wizard?
A. Run the Set-SmbSharecmdlet.
B. Install the File Server Resource Manager role service.
C. Configure Dynamic Access Control and Apply a central access policy.
D. Configure the Advanced system settings.
Answer: B
We offer standard exam questions of Microsoft 70-410 practice test. The standard exams are important if you have never taken a real exam. The accuracy of the Q&As are fully guaranteed and the number is enough to impact you passing the exam.