I recently passed the Microsoft certification exam for 70-410. To celebrate this achievement, I would like to tell you that I used GreatExam Microsoft 70-410 braindumps.
QUESTION 251
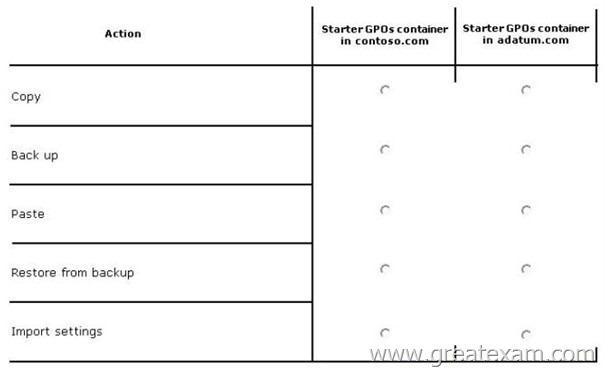
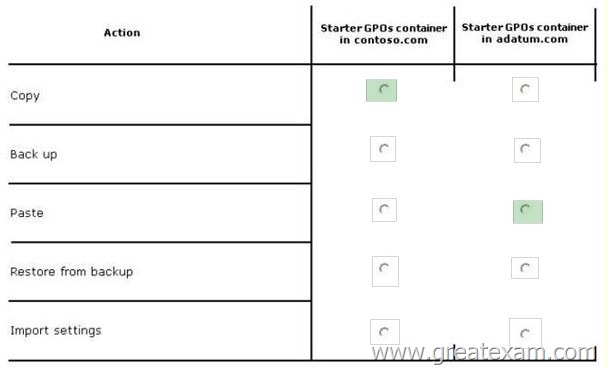
Hotspot Question
Your network contains two Active Directory forests named contoso.com and adatum.com.
A two-way forest trust exists between the forests.
You have custom starter Group Policy objects (GPOs) defined in contoso.com.
You need to ensure that the same set of custom starter GPOs are available in adatum.com.
In the table below, identify which action must be performed for the starter GPOs container in each forest. Make only one selection in two of the rows. Each correct selection is worth one point.
QUESTION 252
Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2. Server1 is a member of a workgroup.
You need to ensure that only members of the Administrators group and members of a group named Group1 can log on locally to Server1.
Which settings should you modify from the Local Security Policy? To answer, select the appropriate settings in the answer area.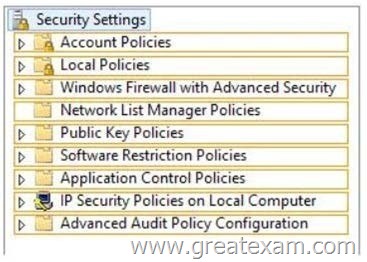
Answer: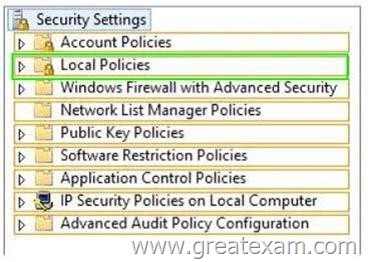
Explanation:
UAC Is controlled by local security policy.
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Option
You can use the Local Security Policy console to modify the behavior of UAC. Start Local Security Policy (Secpol.msc) and open Security Settings\Local Policies\Security Options.
User Account Control (UAC) helps prevent malicious programs (also called malware) from damaging a computer and helps organizations deploy a better-managed desktop. With UAC, applications and tasks always run in the security context of a non-administrator account, unless an administrator specifically authorizes administrator-level access to the system. UAC can block the automatic installation of unauthorized applications and prevent inadvertent changes to system settings.
http://technet.microsoft.com/en-us/library/jj574202.aspx
QUESTION 253
You have a server named Server1. Server1 runs Windows Server 2012 R2 and is located in a perimeter network.
You need to configure a custom connection security rule on Server1. The rule must encrypt network communications across the Internet to a computer at another company.
Which authentication method should you configure in the connection security rule?
A. Advanced
B. User (Kerberos V5)
C. Computer (Kerberos V5)
D. Computer and user (Kerberos V5)
E. Default
Answer: A
Explanation:
You need to make use of Advanced authentication method to ensure that communication is encrypted over the network to the other company from your custom connection security rule on Server1.
http://technet.microsoft.com/en-us/library/bb742516.aspx
QUESTION 254
Your network contains two Active Directory forests named contoso.com and adatum.com.
All servers run Windows Server 2012 R2. A one-way external trust exists between contoso.com and adatum.com. Adatum.com contains a universal group named Group1.
You need to prevent Group1 from being used to provide access to the resources in contoso.com. What should you do?
A. Modify the Managed By settings of Group1.
B. Modify the Allowed to Authenticate permissions in adatum.com.
C. Change the type of Group1 to distribution.
D. Modify the name of Group1.
Answer: B
Explanation:
* Accounts that require access to the customer Active Directory will be granted a special right called Allowed to Authenticate. This right is then applied to computer objects (Active Directory domain controllers and AD RMS servers) within the customer Active Directory to which the account needs access.
* For users in a trusted Windows Server 2008 or Windows Server 2003 domain or forest to be able to access resources in a trusting Windows Server 2008 or Windows Server 2003 domain or forest where the trust authentication setting has been set to selective authentication, each user must be explicitly granted the Allowed to Authenticate permission on the security descriptor of the computer objects (resource computers) that reside in the trusting domain or forest.
QUESTION 255
Your network contains an Active Directory forest named contoso.com. The forest contains a child domain named corp.contoso.com. The network has Microsoft Exchange Server 2010 deployed. You need to create a mail-enabled distribution group.
Which type of group should you create?
A. Domain local
B. Global
C. Local
D. Universal
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/bb726978.aspx
Universal groups Groups that are used to grant permissions on a wide scale throughout a domain tree or forest. Members of global groups include accounts and groups from any domain in the domain tree or forest.
Microsoft Exchange Server 2007: Implementation and Administration
By Jim McBee, Benjamin Craig page 248:
Only universal groups should be used as mail-enabled groups.
QUESTION 256
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2.
The domain contains a user named User1 and a global security group named Group1.
You need to add a new domain controller to the domain.
You install Windows Server 2012 R2 on a new server named DC3.
Which cmdlet should you run next?
A. Add-AdPrincipalGroupMembership
B. Install-AddsDomainController
C. Install WindowsFeature
D. Install AddsDomain
E. Rename-AdObject
F. Set-AdAccountControl
G. Set-AdGroup
H. Set-User
Answer: C
Explanation:
http://www.mustbegeek.com/install-domain-controller-in-server-2012-using-windows-powershell/
It is the 2nd step when installing a DC by powershell on a fresh server.
QUESTION 257
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2. The domain contains a user named User1 and a global security group named Group1. User1 logs on to a client computer named Computer1.
You need to disable the computer account of Computer1.
Which cmdlet should you run?
A. Add-AdPrincipalGroupMembership
B. Install-AddsDomainController
C. Install WindowsFeature
D. Install AddsDomain
E. Rename-AdObject
F. Set-AdAccountControl
G. Set-AdGroup
H. Set-User
Answer: F
Explanation:
http://technet.microsoft.com/en-us/library/ee617249.aspx
Set-ADAccountControl
Enabled
Specifies if an account is enabled. An enabled account requires a password.
This parameter sets the Enabled property for an account object. This parameter also sets the ADS_UF_ACCOUNTDISABLE flag of the Active Directory User Account Control (UAC) attribute. Possible values for this parameter include:
$false or 0
$true or 1
The following example shows how to set this parameter to enable the account.
-Enabled $true
QUESTION 258
Your network contains an Active Directory forest named contoso.com.
The forest contains a single domain. The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2.
The domain contains a user named User1 and a global security group named Group1.
You reconfigure DC2 as a member server in the domain.
You need to add DC2 as the first domain controller in a new domain in the forest.
Which cmdlet should you run?
A. Add-AdPrincipalGroupMembership
B. Install-AddsDomainController
C. Install WindowsFeature
D. Install AddsDomain
E. Rename-AdObject
F. Set-AdAccountControl
G. Set-AdGroup
H. Set-User
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/hh974722.aspx
QUESTION 259
Your network contains an Active Directory domain named contoso.com.
The domain contains a member server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
You create an external virtual switch named Switch1. Switch1 has the following configurations:
– Connection type: External network
– Single-root I/O visualization (SR-IOV): Enabled
– Ten virtual machines connect to Switch1.
You need to ensure that all of the virtual machines that connect to Switch1 are isolated from the external network and can connect to each other only. The solution must minimize network downtime for the virtual machines.
What should you do?
A. Change the Connection type of Switch1 to Internal network.
B. Change the Connection type of Switch1 to Private network.
C. Remove Switch1 and recreate Switch1 as an internal network.
D. Remove Switch1 and recreate Switch1 as a private network.
Answer: D
Explanation:
Original answer is B.
But the correct answer is D.
You cannot change the type of vswitch from external to private when SR-IOV is enabled at vswitch creation -> you need to recreate the vswitch.
QUESTION 260
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 hosts a virtual machine named VM1 that runs Windows Server 2012 R2. VM1 has several snapshots.
You need to modify the snapshot file location of VM1.
What should you do?
A. Right-click VM1, and then click Export…
B. Modify the Hyper-V settings.
C. Delete the existing snapshots, and then modify the settings of VM1.
D. Shut down VM1, and then modify the settings of VM1.
Answer: C
In order for snapshot file location to be changed, all previous snapshots need to be deleted
QUESTION 261
Drag and Drop Question
You have two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts a virtual machine named VM1.
VM1 is currently running. VM1 has a snapshot that was created two weeks ago.
You plan to use Server2 to perform a forensic analysis of the contents of the disk of VM1 from two weeks ago.
You need to ensure that you can view the contents of the disk of VM1 from two weeks ago from Server2.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)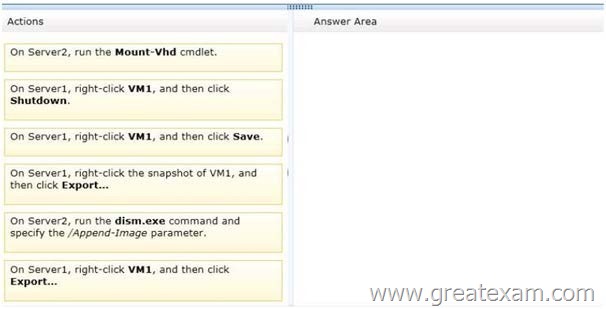
Answer: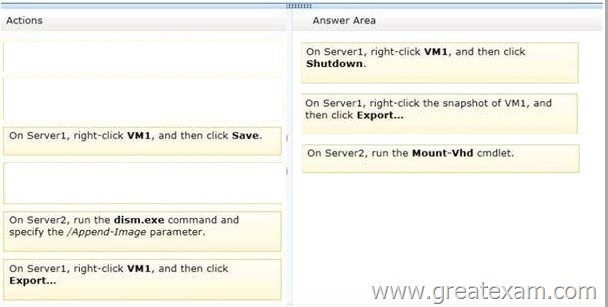
QUESTION 262
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The network contains two subnets. The subnets are configured as shown in the following table.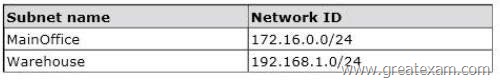
The network contains a member server named Server1 that runs Windows Server 2012 R2.
Server1 has the DHCP Server server role installed. Server1 is configured to lease IP addresses to the two subnets.
You add three new printers to the Warehouse subnet. The printers have static IP addresses.
The IP addresses are consecutive.
You need to create an exclusion range that contains the IP addresses of the printers.
From which node should you configure the exclusion range? To answer, select the appropriate node in the answer area.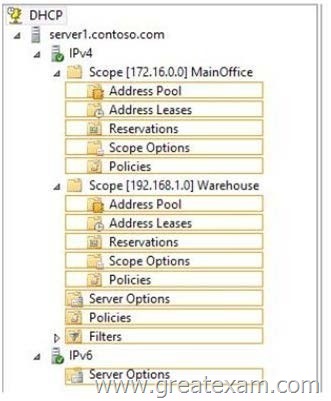
Answer: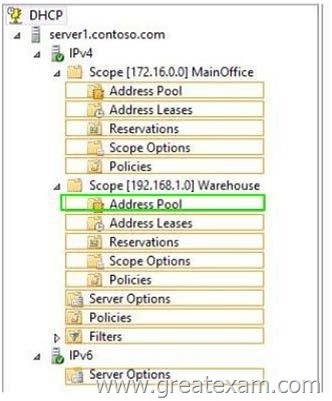
QUESTION 263
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a single location named Site1. The domain contains a server named Server1 that has the DHCP Server server role installed. All client computers receive their IPv4 configurations dynamically. The domain will expand to include a second location named Site2. A server named Server2 will be deployed to Site2. Site1 and Site2 will connect to each other by using a WAN link.
You need to ensure that the clients in both sites receive their IPv4 configurations from Server1.
In the table below, identify which actions must be performed on each server. Make only one selection in each row. Each correct selection is worth one point.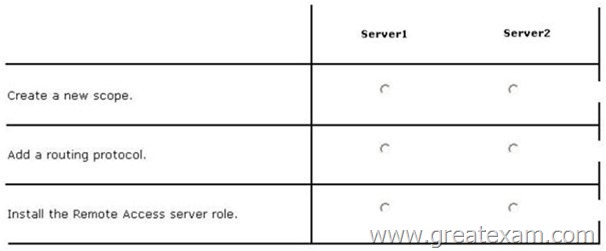
Answer: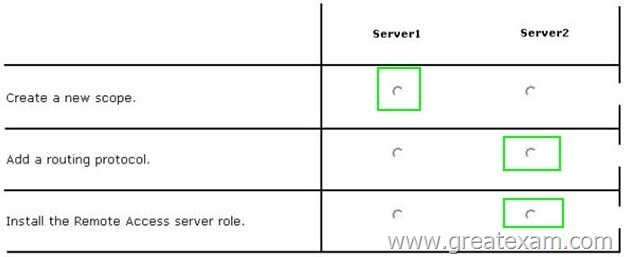
QUESTION 264
You have a server that runs a Server Core installation of Windows Server 2012 R2.
You need to change the DNS server used by IPv6.
What should you do?
A. From Windows PowerShell, run the Set-NetIpv6Protocol cmdlet.
B. From Sconfig, configure the Network Settings.
C. From Windows PowerShell, run the Set-DnsClientServerAddresscmdlet.
D. Run the sc.exe command and specify the config parameter.
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/jj590768.aspx
The Set-DnsClientServerAddress cmdlet sets one or more IP addresses for DNS servers associated with an interface. This cmdlet statically adds DNS server addresses to the interface.
If this cmdlet is used to add DNS servers to the interface, then the DNS servers will override any DHCP configuration for that interface.
PS C:\> Set-DnsClientServerAddress -InterfaceIndex 12 -ServerAddresses (“10.0.0.1″,”10.0.0.2”)
QUESTION 265
Hotspot Question
You have a Hyper-V host named Server1 that runs Windows Server 2008 R2. All of the virtual machines on Server1 use VHDs.
You install the Hyper-V server role on a server named Server2 that runs Windows Server 2012 R2. Server2 has the same hardware configurations as Server1.
You plan to migrate the Hyper-V host from Server1 to Server2 by using the Windows Server Migration Tools.
In the table below, identify what can be migrated by using the Windows Server Migration Tools. Make only one selection in each row. Each correct selection is worth one point.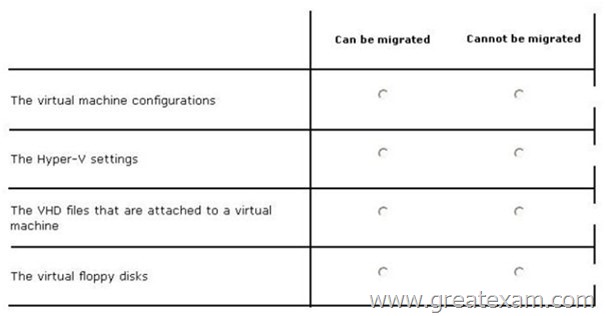
Answer: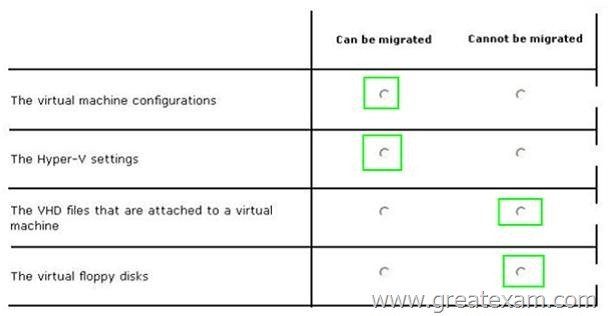
QUESTION 266
You have a server named Server1 that runs Windows Server 2012 R2.
You plan to create a storage pool that will contain a new volume.
You need to create a new 600-GB volume by using thin provisioning. The new volume must use the parity layout.
What is the minimum number of 256-GB disks required for the storage pool?
A. 2
B. 3
C. 4
D. 5
Answer: B
QUESTION 267
You have a server named Server1 that runs Windows Server 2012 R2.
You try to install the Microsoft .NET Framework 3.5 Features feature on Server1, but the installation fails repeatedly.
You need to ensure that the feature can be installed on Server1.
What should you do?
A. Install the Web Server (IIS) server role.
B. Run the Add-WindowsPackagecmdlet.
C. Run the Add-AppxProvisionedPackagecmdlet.
D. Connect Server1 to the Internet.
Answer: D
Explanation:
The files needed are no longer available on the local Hard drive.
We need to connect the server to the Internet.
Note:
Starting with Windows Server 2012 R2 and Windows 8, the feature files for .NET Framework 3.5 (which includes .NET Framework 2.0 and .NET Framework 3.0) are not available on the local computer by default. The files have been removed. Files for features that have been removed in a Features on Demand configuration, along with feature files for .NET Framework 3.5, are available through Windows Update. By default, if feature files are not available on the destination server that is running Windows Server 2012 R2 Preview or Windows Server 2012 R2, the installation process searches for the missing files by connecting to Windows Update.
You can override the default behavior by configuring a Group Policy setting or specifying an alternate source path during installation, whether you are installing by using the Add Roles and Features Wizard GUI or a command line.
QUESTION 268
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that has the DNS Server server role installed. DC1 hosts an Active Directory-integrated zone for the domain. The domain contains a member server named Server1. You install the DNS Server server role on Server1.
You need to ensure that Server1 can respond authoritatively to queries for the existing contoso.com namespace.
Which cmdlets should you run on each server? (To answer, drag the appropriate cmdlets to the correct servers. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)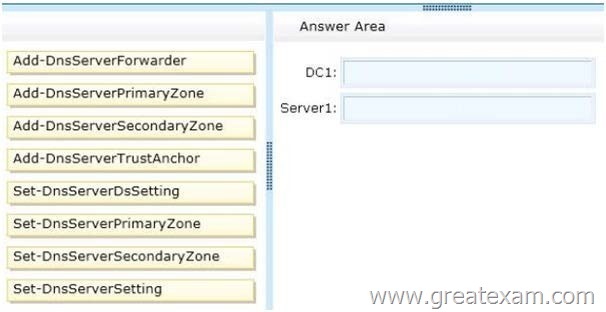
Answer: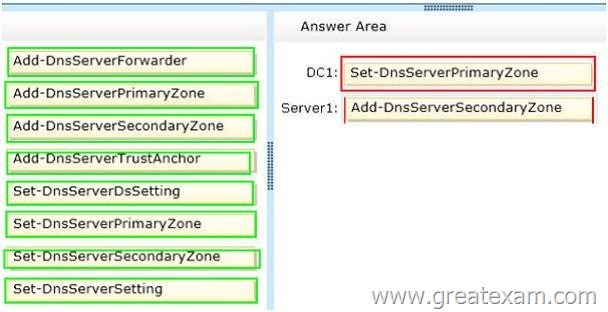
QUESTION 269
Your network contains an Active Directory forest named contoso.com.
The forest contains two domains named contoso.com and child.contoso.com. The forest contains two domain controllers. The domain controllers are configured as shown in the following table.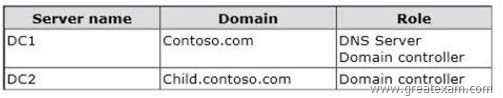
You need to ensure that DC2 can provide authoritative responses for queries to the contoso.com namespace. What should you do?
A. On DC1, create a delegation.
B. On DC1, change the replication scope of the contoso.com zone.
C. On DC2, create a forwarder.
D. On DC2, modify the Zone Transfers settings.
Answer: B
Explanation:
For DC1 to be able to provide authoritative responses to DNS queries the replication scope should be changed accordingly so that it has the zone data for the contoso.com domain.
QUESTION 270
Hotspot Question
You have three servers named Server1, Server2, and DO that run Windows Server 2012 R2. IPv6 addresses and configurations are assigned to all of the servers by using DHCPv6. The IPv6 routing on Server1 is shown in the following table.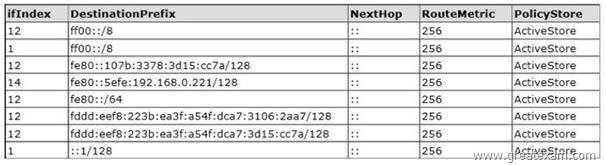
You verify that Server2 can ping the IPv6 address of DC1.
You need to ensure that Server1 can ping the IPv6 address of DC1.
What command should you run on Server1? (To answer, select the appropriate options in the answer area.)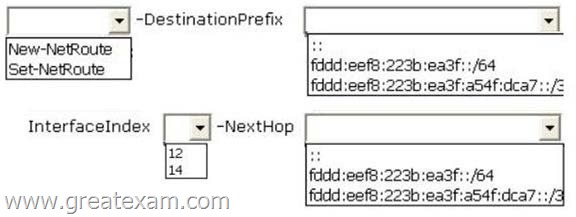
Answer: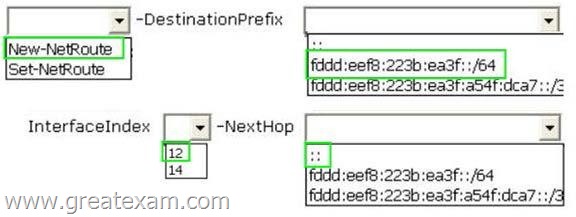
GreatExam 70-410 Questions & Answers VCE dumps are rigorously checked before being put up for sale. So there is nothing irrelevant in 70-410 exam products and you get latest exam questions. It strive to deliver the best 70-410 exam product for top grades in your first attempt.