Microsoft New Released Exam 70-411 exam questions are now can be download from GreatExam! All 442 questions and answers are the latest! 100% exam pass guarantee! Get this IT exam certification in a short time!
QUESTION 21
Your network contains a single Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 that hosts the primary DNS zone for contoso.com.
All servers dynamically register their host names.
You install the new Web servers that host identical copies of your company’s intranet website. The servers are configured as shown in the following table.

You need to use DNS records to load balance name resolution queries for intranet.contoso.com between the two Web servers.
What is the minimum number of DNS records that you should create manually?
A. 1
B. 3
C. 4
D. 6
Answer: B
Explanation:
To create DNS Host (A) Records for all internal pool servers
1. Click Stabrt, click All Programs, click Administrative Tools, and then click DNS.
2. In DNS Manager, click the DNS Server that manages your records to expand it.
3. Click Forward Lookup Zones to expand it.
4. Right-click the DNS domain that you need to add records to, and then click New Host (A or AAAA).
5. In the Name box, type the name of the host record (the domain name will be automatically appended).
6. In the IP Address box, type the IP address of the individual Front End Server and then select Create associated pointer (PTR) record or Allow any authenticated user to update.
DNS records with the same owner name, if applicable.
7. Continue creating records for all member Front End Servers that will participate in DNS Load Balancing.
For example, if you had a pool named pool1.contoso.com and three Front End Servers, you would create the following DNS entries:
http://technet.microsoft.com/en-us/library/cc772506.aspx
http://technet.microsoft.com/en-us/library/gg398251.aspx
QUESTION 22
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Access server role installed.
You need to configure the ports on Server1 to ensure that client computers can establish VPN connections to Server1. The solution must NOT require the use of certificates or pre-shared keys.
What should you modify?
To answer, select the appropriate object in the answer area.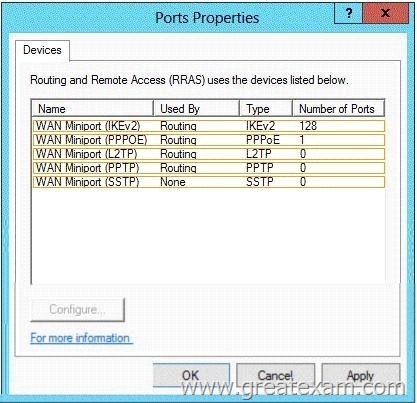
Answer: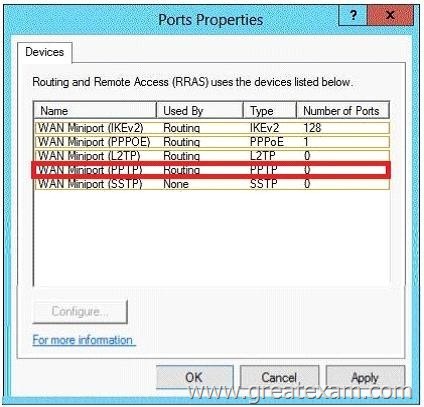
Explanation:
The four types of tunneling protocols used with a VPN/RAS server running on Windows Server 2012 include:
Point-to-Point Tunneling Protocol (PPTP):
A VPN protocol based on the legacy Point-to-Point protocol used with modems.
The PPTP specification does not describeencryption or authentication features and relies on the Point-to-Point Protocol being tunneled to implement security functionality.
Layer 2 Tunneling Protocol (L2TP): Used with IPsec to provide security.
L2TP supports either computer certificates or a preshared key as the authentication method for IPsec. IKEv2: IKE is short for Internet Key Exchange, which is a tunneling protocol that uses IPsec Tunnel Mode protocol. The message is encrypted with one of the following protocols by using encryption keys that are generated from the IKEv2 negotiation process.
Secure Socket Tunneling Protocol (SSTP): Introduced with Windows Server 2008, which uses the HTTPS protocol over TCP port 443 to pass traffic through firewalls
http://en.wikipedia.org/wiki/Point-to-Point_Tunneling_Protocol
QUESTION 23
Hotspot Question
You have a server named Servers that runs Windows Server 2012 R2. Servers has the Windows Deployment Services server role installed.
Server5 contains several custom images of Windows 8.
You need to ensure that when 32-bit client computers start by using PXE, the computers automatically install an image named Image 1.
What should you configure?
To answer, select the appropriate tab in the answer area.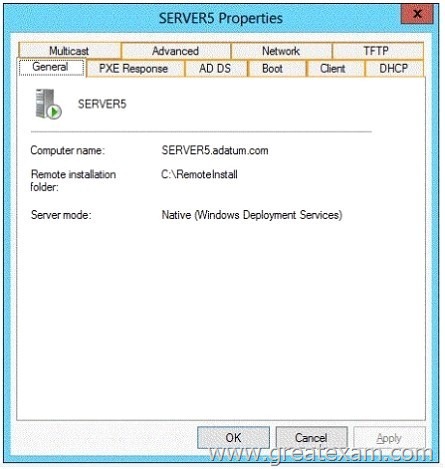
Answer: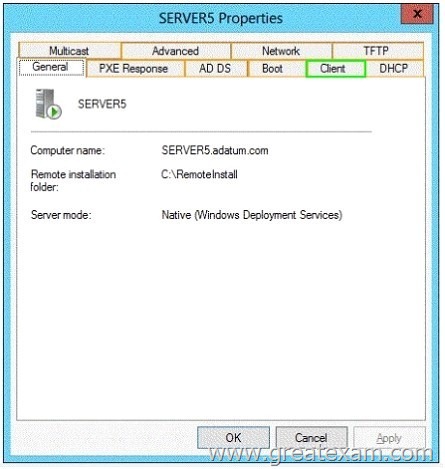
Explanation:
On the Register Client separate answer files can be stored for unattended installation for different processor architectures
QUESTION 24
You have a cluster named Cluster1 that contains two nodes. Both nodes run Windows Server 2012 R2. Cluster1 hosts a virtual machine named VM1 that runs Windows Server 2012 R2.
You configure a custom service on VM1 named Service1.
You need to ensure that VM1 will be moved to a different node if Service1 fails.
Which cmdlet should you run on Cluster1?
A. Add-ClusterVmMonitoredItem
B. Add-ClusterGenericServiceRole
C. Set-ClusterResourceDependency
D. Enable VmResourceMetering
Answer: A
Explanation:
The Add-ClusterVMMonitoredItem cmdlet configures monitoring for a service or an Event
Tracing for Windows (ETW) event so that it is monitored on a virtual machine. If the service fails or the event occurs, then the system responds by taking an action based on the failover configuration for the virtual machine resource. For example, the configuration might specify that the virtual machine be restarted.
QUESTION 25
Your company has a main office and a branch office.
The main office contains a server that hosts a Distributed File System (DFS) replicated folder.
You plan to implement a new DFS server in the branch office.
You need to recommend a solution that minimizes the amount of network bandwidth used to perform the initial synchronization of the folder to the branch office.
You recommend using the Export-DfsrClone and Import-DfsrClonecmdlets.
Which additional command or cmdlet should you include in the recommendation?
A. Robocopy.exe
B. Synchost.exe
C. Export-BcCachePackage
D. Sync-DfsReplicationGroup
Answer: A
Explanation:
By preseeding files before you set up DFS Replication, add a new replication partner, or replace a server, you can speed up initial synchronization and enable cloning of the DFS Replication database in Windows Server 2012 R2. The Robocopy method is one of several preseeding methods
QUESTION 26
Your network contains an Active Directory domain named contoso.com.
You have several Windows PowerShell scripts that execute when users log on to their client computer.
You need to ensure that all of the scripts execute completely before the users can access their desktop.
Which setting should you configure?
To answer, select the appropriate setting in the answer area.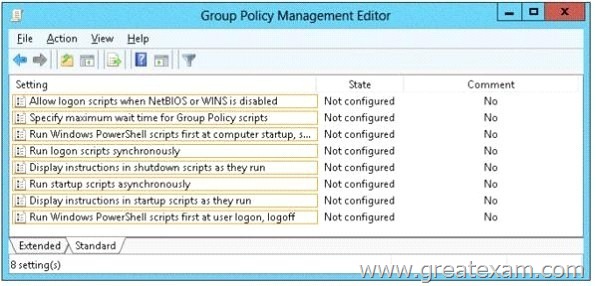
Answer: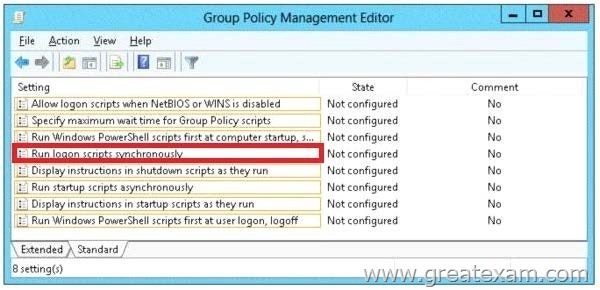
Explanation:
http://technet.microsoft.com/en-us/library/cc738773(v=ws.10).aspx
Run logon scripts synchronously
Directs the system to wait for logon scripts to finish running before it starts the Windows Explorer interface program and creates the desktop.
If you enable this policy, Windows Explorer does not start until the logon scripts have finished running. This setting assures that logon script processing is complete before the user starts working, but it can delay the appearance of the desktop.
If you disable this policy or do not configure it, the logon scripts and Windows Explorer are not synchronized and can run simultaneously.
QUESTION 27
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise. A Group Policy object (GPO) named GPO1 is linked to OU1.
You make a change to GPO1.
You need to force all of the computers in OU1 to refresh their Group Policy settings immediately. The solution must minimize administrative effort.
Which tool should you use?
A. Server Manager
B. Active Directory Users and Computers
C. The Gpupdate command
D. Group Policy Management Console (GPMC)
Answer: D
Explanation:
Starting with Windows Server 2012 and Windows 8, you can now remotely refresh Group Policy settings for all computers in an OU from one central location through the Group Policy Management Console (GPMC). Or you can use the Invoke- GPUpdatecmdlet to refresh Group Policy for a set of computers, not limited to the OU structure, for example, if the computers are located in the default computers container.
http://technet.microsoft.com/en-us//library/jj134201.aspx http://blogs.technet.com/b/grouppolicy/archive/2012/11/27/group-policy-in-windows-server-2012-using-remote-gpupdate.aspx
QUESTION 28
Your network contains an Active Directory domain named contoso.com. Domain controllers run either Windows Server 2008, Windows Server 2008 R2, or Windows Server 2012 R2.
You have a Password Settings object (PSOs) named PSO1.
You need to view the settings of PSO1.
Which tool should you use?
A. Group Policy Management
B. Server Manager
C. Get-ADAccountResultantPasswordReplicationPolicy
D. Active Directory Administrative Center
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc770848(v=ws.10).aspx
Incorrect:
* Get-ADFineGrainedPasswordPolicy
Gets one or more Active Directory fine grained password policies.
* To store fine-grained password policies, Windows Server 2008 includes two new object classes in the Active Directory Domain Services (AD DS) schema:
Password Settings Container
Password Settings
The Password Settings Container (PSC) object class is created by default under the System container in the domain. It stores the Password Settings objects (PSOs) for that domain.
QUESTION 29
Your network contains an Active Directory domain named contoso.com. The domain contains more than 100 Group Policy objects (GPOs). Currently, there are no enforced GPOs.
You need to prevent all of the GPOs at the site level and at the domain level from being applied to users and computers in an organizational unit (OU) named OU1.
You want to achieve this goal by using the minimum amount of Administrative effort.
What should you use?
A. dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gpresult
E. Gptedit.msc
F. Import-GPO
G. Import-GPO
H. Restore-GPO
I. Set-GPInheritance
J. Set-GPLink
K. Set-GPPermission
L. Gpupdate
M. Add-ADGroupMember
Answer: I
Explanation:
The cmdlet Set-GPInheritance enable or disable inheritance for a given organizational unit and thus prevents GPOs that are linked to a higher level, are applied to the objects of being surrounded OU.
The following call disables inheritance parent GPOs for OU CBTest the root of the domain:
Set-GPinheritance -target “ou = contosoTest, dc = contoso, dc = com” -IsBlocked Yes
http://technet.microsoft.com/en-us/library/ee461032.aspx
http://technet.microsoft.com/en-us/library/cc757050.aspx
QUESTION 30
Your network contains an Active Directory domain named contoso.com. The domain contains more than 100 Group Policy objects (GPOs). Currently, there are no enforced GPOs.
You have two GPOs linked to an organizational unit (OU) named OU1.
You need to change the precedence order of the GPOs.
What should you use?
A. Dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gpresult
E. Gptedit.msc
F. Import-GPO
G. Restore-GPO
H. Set-GPInheritance
I. Set-GPLink
J. Set-GPPermission
K. Gpupdate
L. Add-ADGroupMember
Answer: I
Explanation:
The Set-GPLink cmdlet sets the properties of a GPO link.
You can set the following properties:
— Enabled. If the GPO link is enabled, the settings of the GPO are applied when Group Policy is processed for the site, domain or OU.
— Enforced. If the GPO link is enforced, it cannot be blocked at a lower-level (in the Group Policy processing hierarchy) container.
— Order. The order specifies the precedence that the settings of the GPO take over conflicting settings in other GPOs that are linked (and enabled) to the same site, domain, or OU. http://technet.microsoft.com/en-us/library/ee461022.aspx
QUESTION 31
Your network contains an Active Directory domain named contoso.com. The domain contains more than 100 Group Policy objects (GPOs). Currently, there are no enforced GPOs.
You need to provide an Administrator named Admin1 with the ability to create GPOs in the domain. The solution must not provide Admin1 with the ability to link GPOs.
What should you use?
A. dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gpresult
E. Gptedit.msc
F. Import-GPO
G. Restore-GPO
H. Set-GPInheritance
I. Set-GPLink
J. Set-GPPermission
K. Gpupdate
L. Add-ADGroupMember
Answer: J
Explanation:
http://technet.microsoft.com/en-us/library/ee461038.aspx
QUESTION 32
Your network contains an Active Directory domain named contoso.com. The domain contains more than 100 Group Policy objects (GPOs). Currently, there are no enforced GPOs. The domain contains a GPO named GPO1. GPO1 contains several Group Policy preferences.
You need to view all of the preferences configured in GPO1.
What should you use?
A. dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gpresult
E. Gptedit.msc
F. Import-GPO
G. Restore-GPO
H. Set-GPInheritance
I. Set-GPLink
J. Set-GPPermission
K. Gpupdate
L. Add-ADGroupMember
Answer: B
Explanation:
The Get-GPOReport cmdlet generates a report in either XML or HTML format that describes properties and policy settings for a specified GPO or for all GPOs in a domain. The information that is reported for each GPO includes: details, links, security filtering, WMI filtering, delegation, and computer and user configuration
http://technet.microsoft.com/en-us/library/ee461027.aspx http://cmdlet.wordpress.com/2011/08/24/episode-3-get-gporeport
QUESTION 33
Your network contains an Active Directory domain named contoso.com. The domain contains more than 100 Group Policy objects (GPOs). Currently, there are no enforced GPOs.
A network Administrator accidentally deletes the Default Domain Policy GPO.
You do not have a backup of any of the GPOs.
You need to recreate the Default Domain Policy GPO.
What should you use?
A. dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gptedit.msc
E. Import-GPO
F. Restore-GPO
G. Set-GPInheritance
H. Set-GPLink
I. Set-GPPermission
J. Gpupdate
K. Add-ADGroupMember
Answer: A
Explanation:
Restores the default Group Policy objects to their original state (that is, the default state after initial installation).
QUESTION 34
Your network contains an Active Directory domain named contoso.com. The domain contains more than 100 Group Policy objects (GPOs). Currently, there are no enforced GPOs. The domain is renamed to adatum.com. Group Policies no longer function correctly.
You need to ensure that the existing GPOs are applied to users and computers.
You want to achieve this goal by using the minimum amount of Administrative effort.
What should you use?
A. dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gpresult
E. Gptedit.msc
F. Import-GPO
G. Restore-GPO
H. Set-GPInheritance
I. Set-GPLink
J. Set-GPPermission
K. Gpupdate
L. Add-ADGroupMember
Answer: C
Explanation:
You can use the gpfixup command-line tool to fix the dependencies that Group Policy objects (GPOs) and Group Policy links in Active Directory Domain Services (AD DS) have on Domain Name System (DNS) and NetBIOS names after a domain rename operation.
QUESTION 35
Your network contains an Active Directory domain named contoso.com. The domain contains more than 100 Group Policy objects (GPOs). Currently, there are no enforced GPOs. The domain contains a top-level organizational unit (OU) for each department. A group named Group1 contains members from each department.
You have a GPO named GPO1 that is linked to the domain.
You need to configure GPO1 to apply settings to Group1 only.
What should you use?
A. dcgpofix
B. Get-GPOReport
C. Gpfixup
D. Gpresult
E. Gptedit.msc
F. Import-GPO
G. Restore-GPO
H. Set-GPInheritance
I. Set-GPLink
J. Set-GPPermission
K. Gpupdate
L. Add-ADGroupMember
Answer: J
Explanation:
J. Set-GPPermission grants a level of permissions to a security principal (user, security group, or computer) for one GPO or all the GPOs in a domain. You use the TargetName and TargetType parameters to specify a user, security group, or computer for which to set the permission level.
-Replace <SwitchParameter>
Specifies that the existing permission level for the group or user is removed before the new permission level is set. If a security principal is already granted a permission level that is higher than the specified permission level and you do not use the Replace parameter, no change is made. http://technet.microsoft.com/en-us/library/ee461038.aspx
QUESTION 36
Your network contains an Active Directory domain named contoso.com.
A user named User1 creates a central store and opens the Group Policy Management Editor as shown in the exhibit.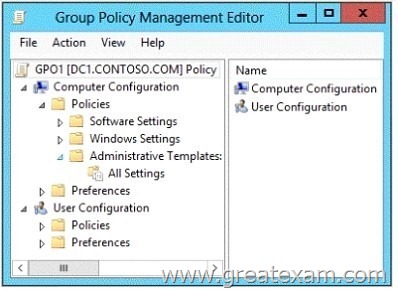
You need to ensure that the default Administrative Templates appear in GPO1.
What should you do?
A. Link a WMI filter to GPO1.
B. Add User1 to the Group Policy Creator Owners group.
C. Configure Security Filtering in GPO1.
D. Copy files from %Windir%\PolicyDefinitions to the central store.
Answer: D
Explanation:
In earlier operating systems, all the default Administrative Template files are added to the ADM folder of a Group Policy object (GPO) on a domain controller. The GPOs are stored in the SYSVOL folder. The SYSVOL folder is automatically replicated to other domain controllers in the same domain.
A policy file uses approximately 2 megabytes (MB) of hard disk space. Because each domain controller stores a distinct version of a policy, replication traffic is increased.
In Group Policy for Windows Server 2008 and Windows Vista, if you change Administrative template policy settings on local computers, Sysvol will not be automatically updated with the new .ADMX or .ADML files. This change in behavior is implemented to reduce network load and disk storage requirements, and to prevent conflicts between .ADMX files and. ADML files when edits to Administrative template policy settings are made across different locales. To make sure that any local updates are reflected in Sysvol, you must manually copy the updated .ADMX or .ADML files from the PolicyDefinitions file on the local computer to the Sysvol\PolicyDefinitions folder on the appropriate domain controller.
To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder on a domain controller. The Central Store is a file location that is checked by the Group Policy tools. The Group Policy tools use any .admx files that are in the Central Store. The files that are in the Central Store are later replicated to all domain controllers in the domain.
To create a Central Store for .admx and .adml files, create a folder that is named PolicyDefinitions in the following location:
\\FQDN\SYSVOL\FQDN\policies
http://support.microsoft.com/kb/929841
QUESTION 37
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 P.2. Server1 has the Network Policy and Access Services server role installed.
Your company’s security policy requires that certificate-based authentication must be used by some network services.
You need to identify which Network Policy Server (NPS) authentication methods comply with the security policy.
Which two authentication methods should you identify?
(Each correct answer presents part of the solution. Choose two.)
A. MS-CHAP
B. PEAP-MS-CHAP v2
C. Chap
D. EAP-TLS
E. MS-CHAP v2
Answer: BD
Explanation:
PEAP is similar in design to EAP-TTLS, requiring only a server-side PKI certificate to create a secure TLS tunnel to protect user authentication, and uses server- side public key certificates to authenticate the server. When you use EAP with a strong EAP type, such as TLS with smart cards or TLS with certificates, both the client and the server use certificates to verify their identities to each other.
QUESTION 38
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Windows Deployment Services server role installed.
Server1 contains two boot images and four install images.
You need to ensure that when a computer starts from PXE, the available operating system images appear in a specific order.
What should you do?
A. Modify the properties of the boot images.
B. Create a new image group.
C. Modify the properties of the install images.
D. Modify the PXE Response Policy.
Answer: C
Explanation:
installation images are the operating system images that you deploy to the client computer. Start images are the images with which you start a client computer to perform an operating system installation. Boot images contain Windows PE and the Windows Deployment Services client.
The order of the display of images can about the value of priority on the register general are controlled in the properties of the images:
QUESTION 39
Your network contains an Active Directory domain named contoso.com. Domain controllers run either Windows Server 2008, Windows Server 2008 R2, or Windows Server 2012 R2.
You have a Password Settings object (PSOs) named PSO1.
You need to view the settings of PSO1.
Which tool should you use?
A. Get-ADFineGrainedPasswordPolicy
B. Get-ADAccountResultantPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicy
D. Get-ADDefaultDomainPasswordPolicy
Answer: A
Explanation:
A. Gets one or more Active Directory fine grained password policies.
B. Gets the resultant password replication policy for an Active Directory account.
C. Gets the members of the allowed list or denied list of a read-only domain controller’s password replication policy
D. Gets the default password policy for an Active Directory domain. http://technet.microsoft.com/en-us/library/ee617231.aspx
ttp://technet.microsoft.com/en-us/library/ee617227.aspx
http://technet.microsoft.com/en-us/library/ee617207.aspx
http://technet.microsoft.com/en-us/library/ee617244.aspx
QUESTION 40
You have a failover cluster that contains five nodes. All of the nodes run Windows Server 2012 R2. All of the nodes have BitLocker Drive Encryption (BitLocker) enabled.
You enable BitLocker on a Cluster Shared Volume (CSV).
You need to ensure that all of the cluster nodes can access the CSV.
Which cmdlet should you run next?
A. Unblock-Tpm
B. Add-BitLockerKeyProtector
C. Remove-BitLockerKeyProtector
D. Enable BitLockerAutoUnlock
Answer: B
Explanation:
Add an Active Directory Security Identifier (SID) to the CSV disk using the Cluster Name Object (CNO) The Active Directory protector is a domain security identifier (SID) based protector for protecting clustered volumes held within the Active Directory infrastructure. It can be bound to a user account, machine account or group. When an unlock request is made for a protected volume, the BitLocker service interrupts the request and uses the BitLocker protect/unprotect APIs to unlock or deny the request.
For the cluster service to selfmanage BitLocker enabled disk volumes, an administrator must add the Cluster Name Object (CNO), which is the Active Directory identity associated with the Cluster Network name, as a BitLocker protector to the target disk volumes.
Add-BitLockerKeyProtector <drive letter or CSV mount point> –
ADAccountOrGroupProtector – ADAccountOrGroup $cno
GreatExam gives the latest, authoritative and complete 70-411 braindumps for 70-411 exam, because of that, all of our candidates pass 70-411 certification without any problem. The biggest feature is the regular update of 70-411 PDF and VCE, which keeps our candidates’ knowledge up to date and ensures their 70-411 exam success.